Allow Non-Admin Users to Manage Their Desktop Icons Using Intune
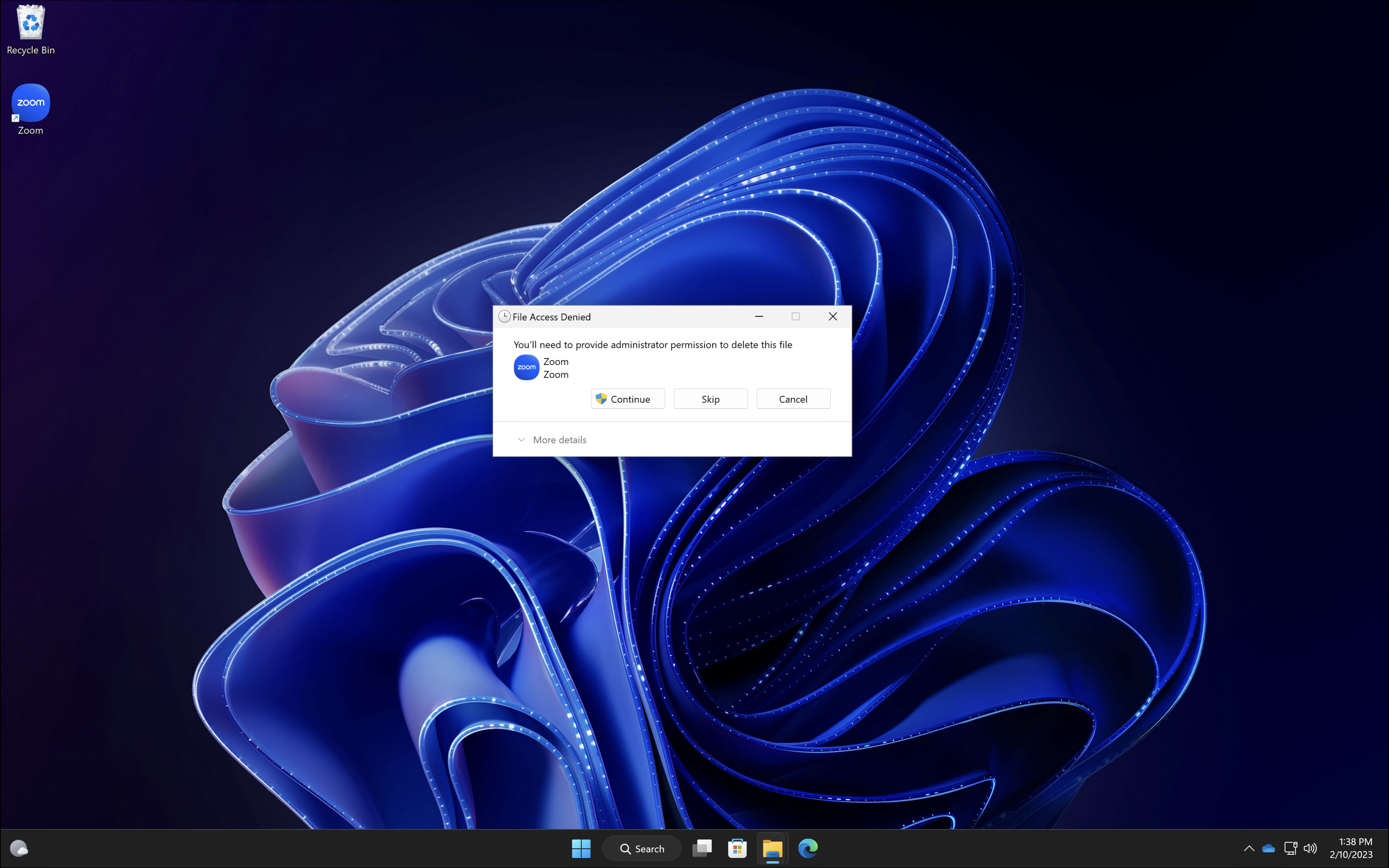
Many IT organizations do not allow their end users to be local administrators on company endpoints, and for good reason. But one issue I have ran across is that some applications install an icon on the public desktop (C:\Users\Public\Desktop) and the end user is unable to delete the icon as it requires administrative rights. Using PowerShell, we can modify the ACL of the public desktop folder and allow our non-admin users to delete these shortcuts.
 Copy the PowerShell script below and save it somewhere we can reference it later. This script modifies the permissions for the folder ‘C:\Users\Public\Desktop’ and adds the ‘authenticated users‘ entity to it with the ‘modify’ permission.
Copy the PowerShell script below and save it somewhere we can reference it later. This script modifies the permissions for the folder ‘C:\Users\Public\Desktop’ and adds the ‘authenticated users‘ entity to it with the ‘modify’ permission.
$folderPath = "C:\Users\Public\Desktop"
$acl = Get-Acl $folderPath
$user = New-Object System.Security.Principal.SecurityIdentifier('S-1-5-11')
$rule = New-Object System.Security.AccessControl.FileSystemAccessRule ($user,"Modify", "ContainerInherit,ObjectInherit", "None", "Allow")
$acl.SetAccessRule($rule)
Set-ACL $folderPath $acl
Open a web browser and navigate to Intune.Microsoft.com > Devices > Scripts and Add a new Script. Give your new script a proper name so other administrators understand what it is doing.
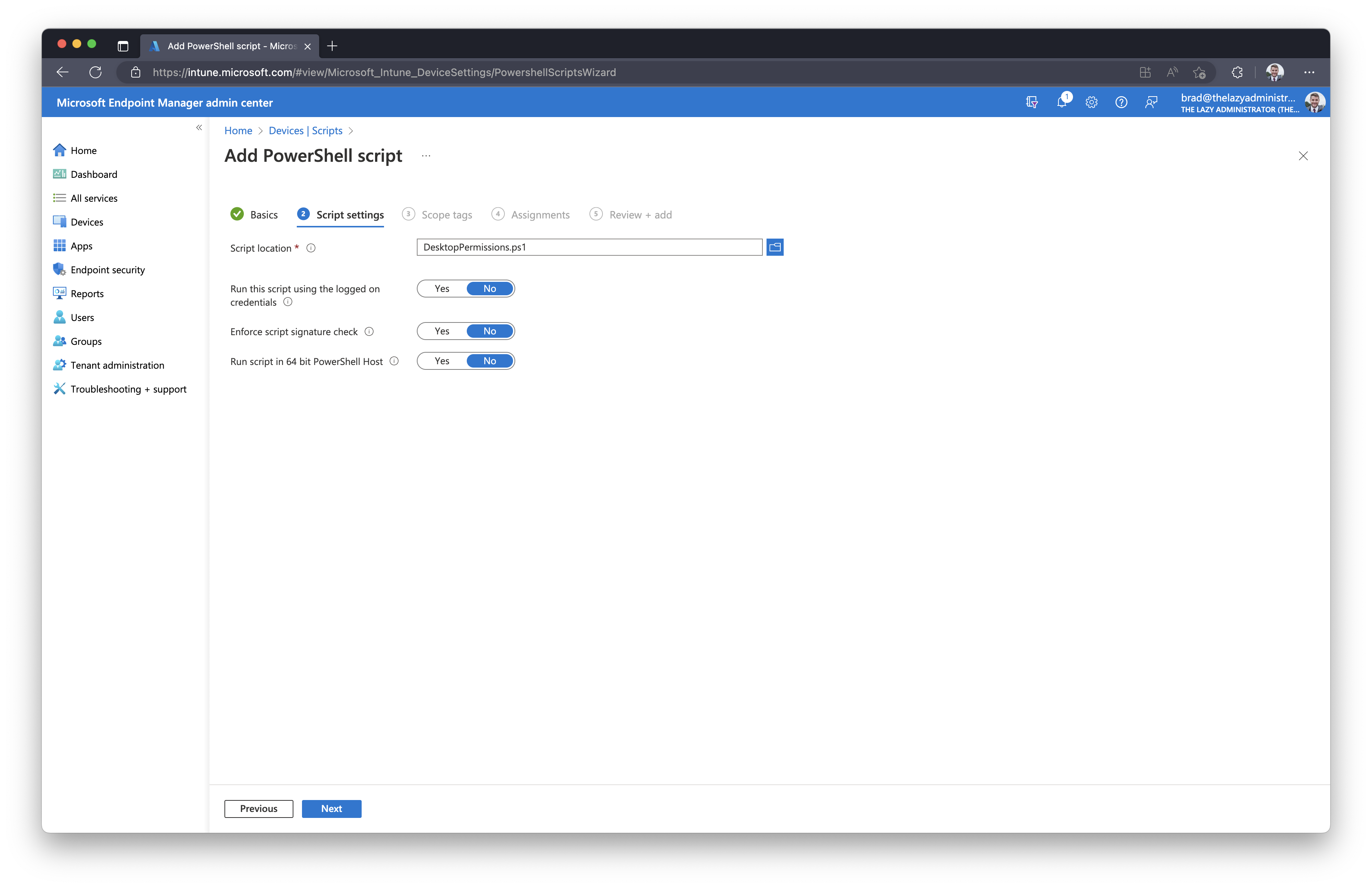
For ‘Script Location’ select the location of the script you made earlier. The other settings can be kept as ‘No’
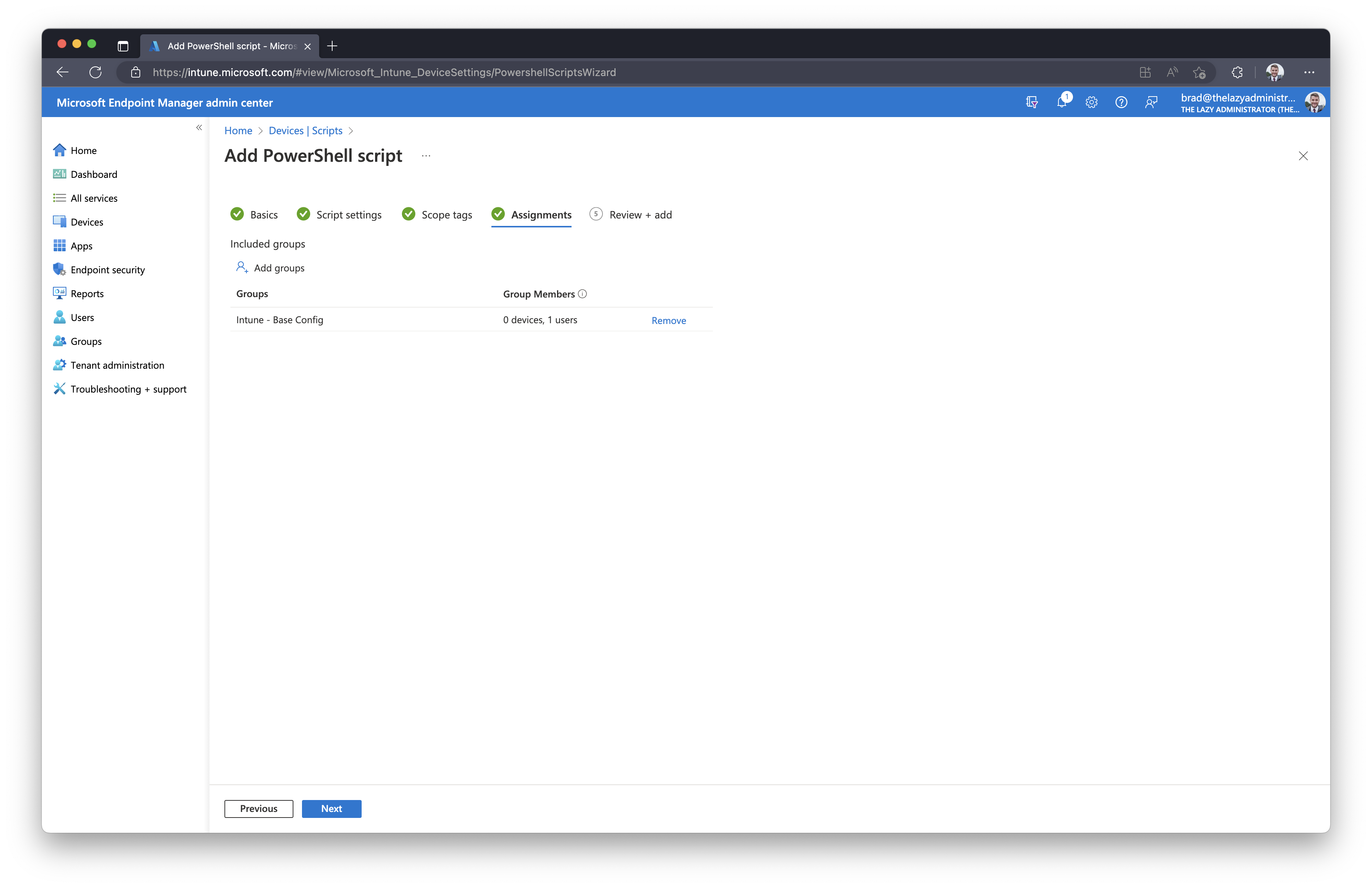
Under, “Assignments”, assign it to a group.
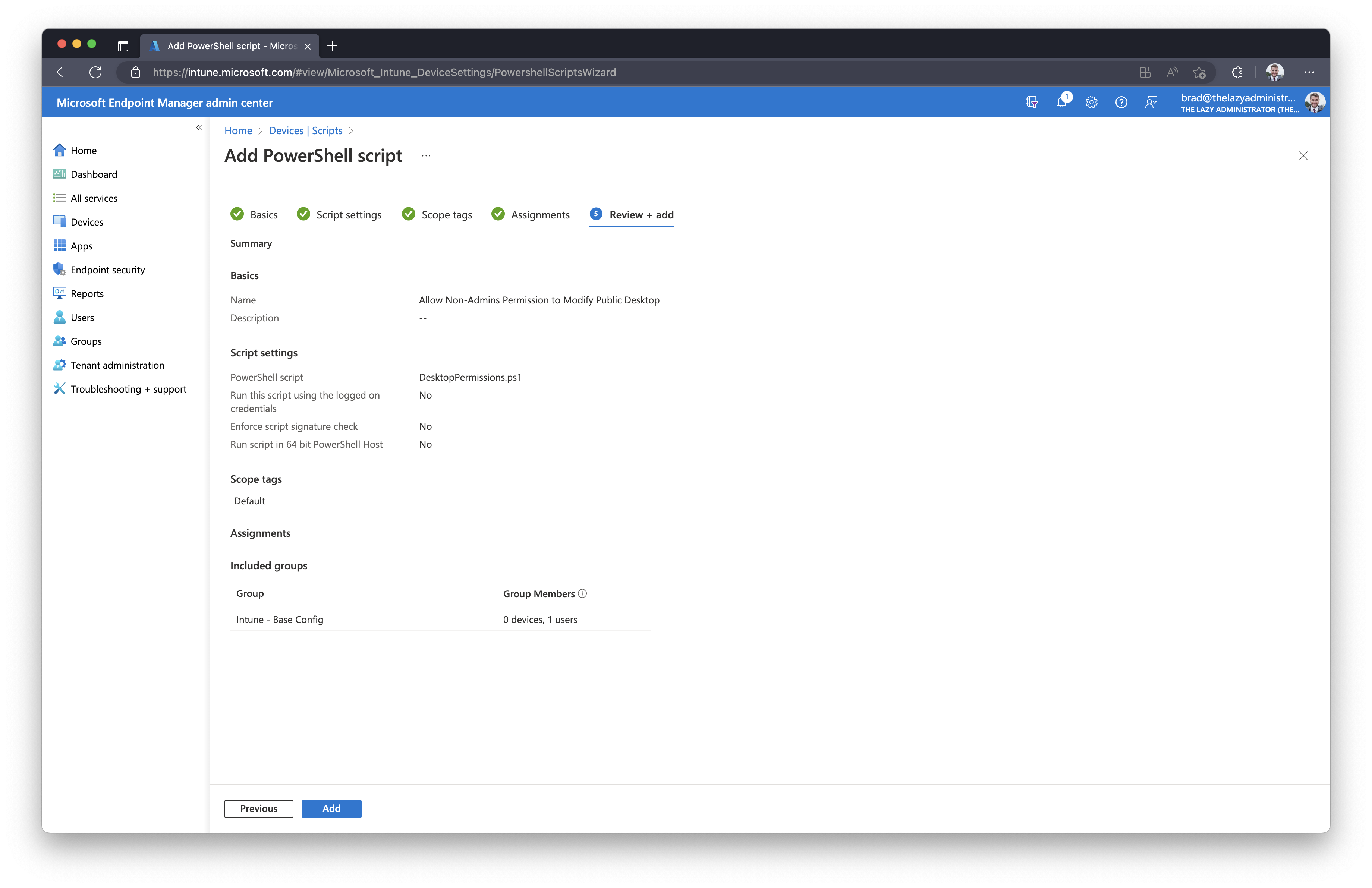
 Finally, in the ‘Review + add” section, review your new PowerShell script. If there are no issues, click “Add” to finish and deploy it to your endpoints/users.
Finally, in the ‘Review + add” section, review your new PowerShell script. If there are no issues, click “Add” to finish and deploy it to your endpoints/users.
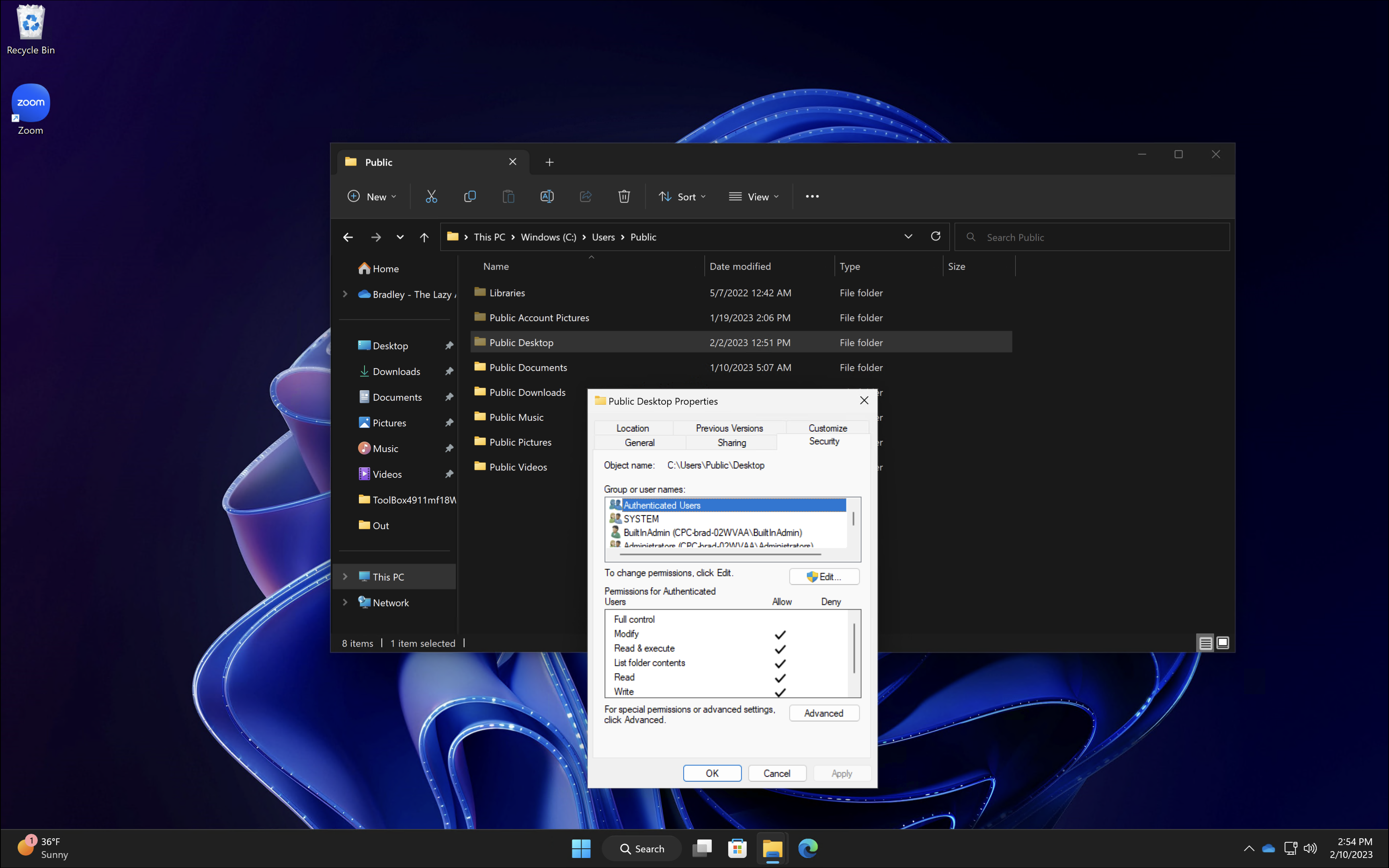
Going back to our endpoint, after the script has been applied, we can check the security permissions and see ‘Authenticated Users’ is now added. Now, when our end user attempts to delete a shortcut they no longer get a UAC prompt.

My name is Bradley Wyatt; I am a 5x Microsoft Most Valuable Professional (MVP) in Microsoft Azure and Microsoft 365. I have given talks at many different conferences, user groups, and companies throughout the United States, ranging from PowerShell to DevOps Security best practices, and I am the 2022 North American Outstanding Contribution to the Microsoft Community winner.
One thought on “Allow Non-Admin Users to Manage Their Desktop Icons Using Intune”
You are my hero today, thank you.