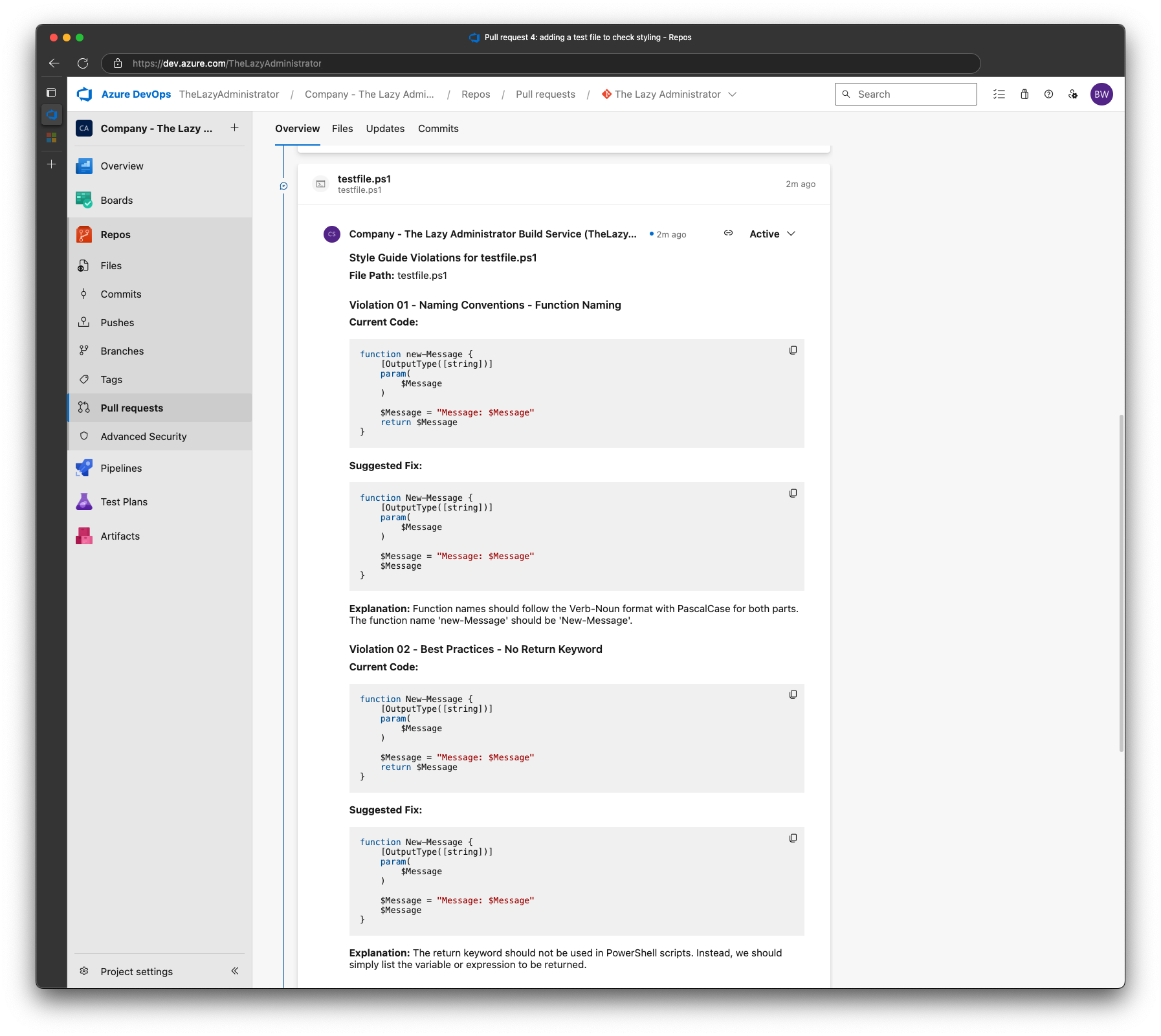
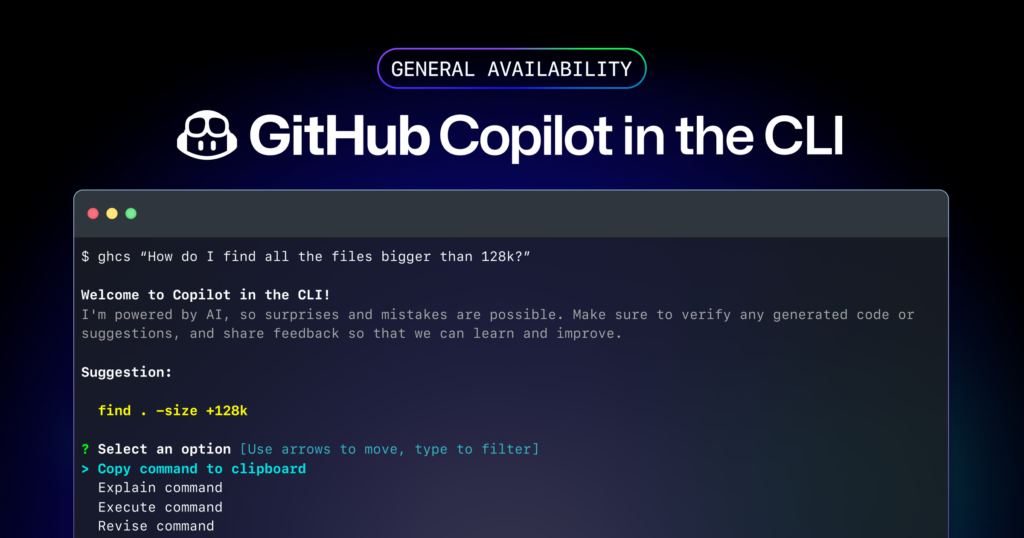
Detect Modified SharePoint List Items and Retrieve Old Values in Sharepoint Using Logic Apps
Overview
I currently have a SharePoint list with an identity (person or group) column called “Owners,” where I can search for employees and add them to a list item. I then want to e-mail newly added people that they have been added to a list item so they can go and review the details of it.
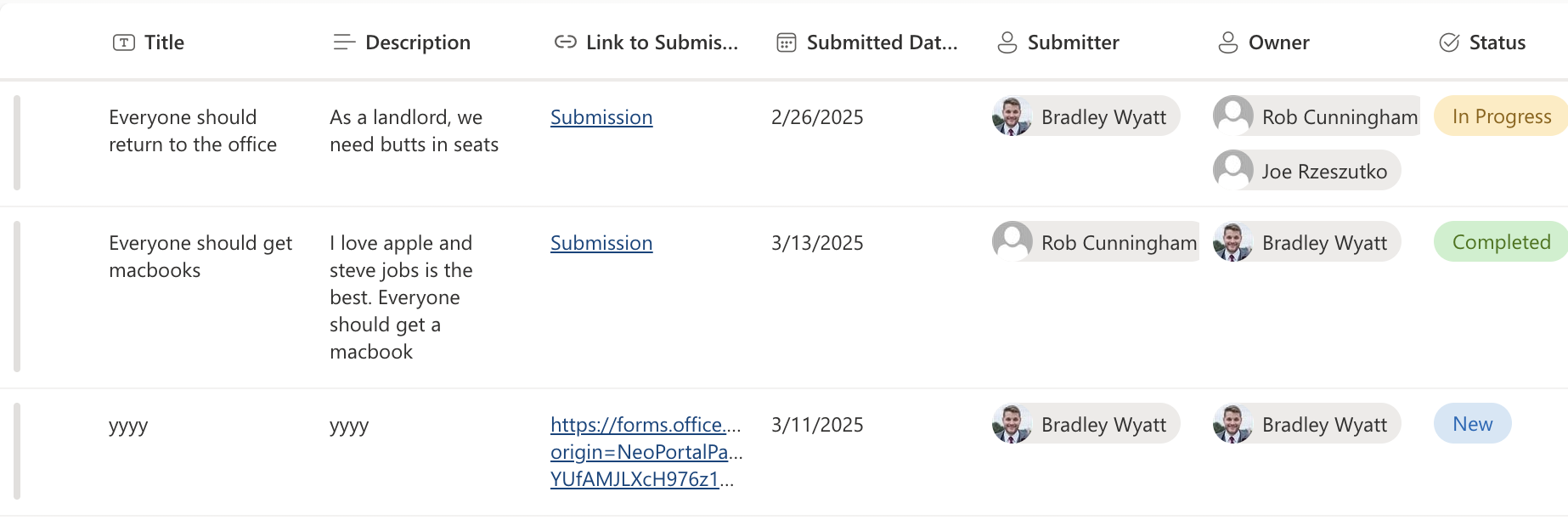
While SharePoint does have an ‘automate’ feature where you can detect a list item’s column is modified, the only option is to send an email to all the people that are currently in that column. So, if you add a new person, it will re-email everyone who is already there. The other issue is that the e-mail says (below) is non-descript, so your users will be confused about why they are getting it.
Logic Apps does have a trigger that is “When an item is modified,” but its output is the current … Continue...