Improve your Azure Multi-Factor Authentication Notifications
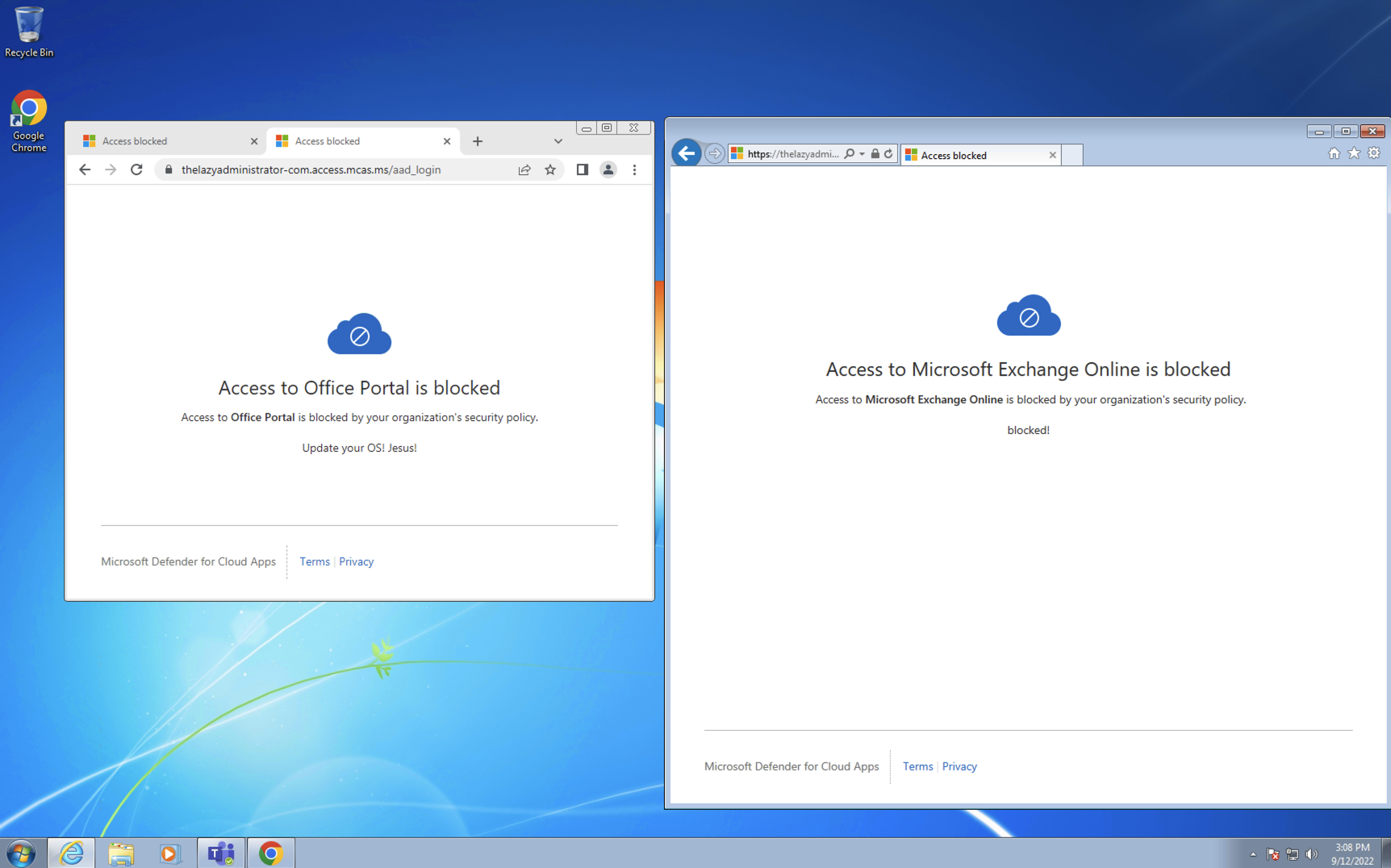
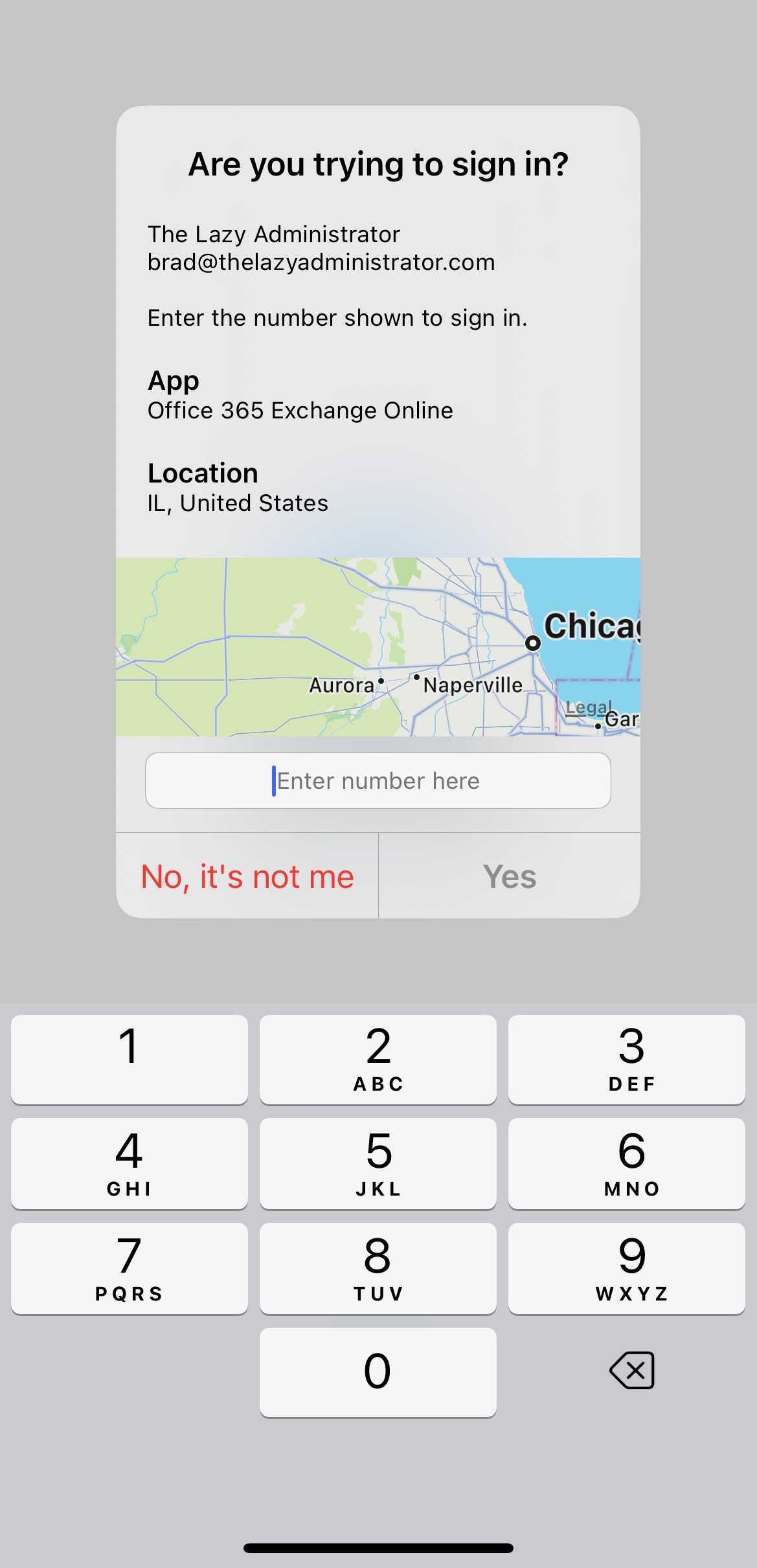
Recently, Uber appeared to be hacked in what is called a MFA Fatigue attack. The attacker continuously sent MFA requests to an end user hoping they would accidentally approve one of them. Microsoft has several items to help prevent MFA fatigue attacks that you can configure and enable for your end users. Traditionally, MFA notifications are push notifications where a user can either accept or deny the request. Some improvements to this have been multiple number options where the end user must select one of four numbers that is presented on the screen they are logging into. The problem with this is that leaves a 1 in 4 chance an accidental selection may result in unauthorized access.
Configure Fraud Alerts
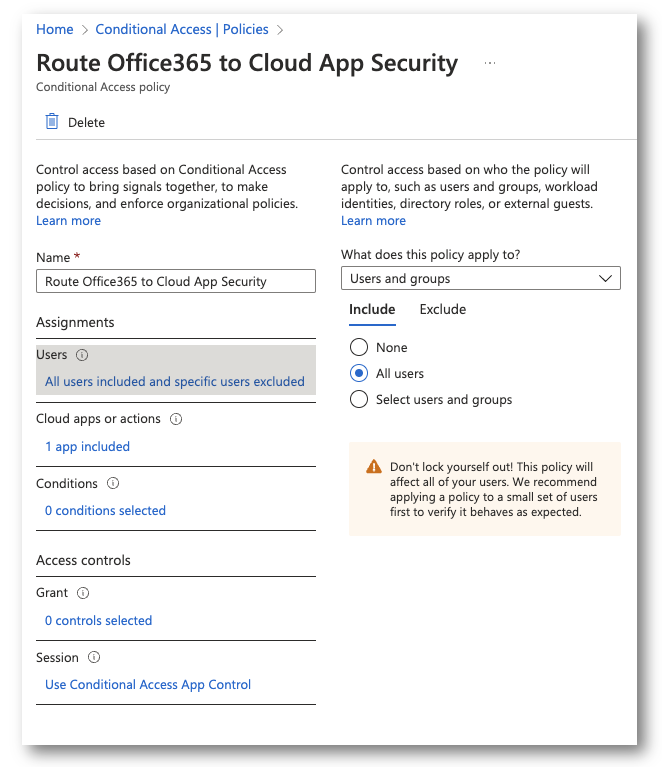
Fraud Alerts allow your users to report fraud if they receive a two-step verification request that they didn’t initiate and automatically block their account from sign-on.
Go to the Azure … Continue...