Configure Autopilot Hybrid Azure-AD and ADDS Domain Join
Table of Contents
Prerequisites
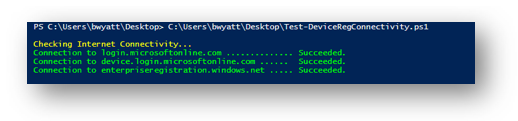
Hybrid Azure AD join requires devices to have access to the following Microsoft resources from inside your organization’s network. These addresses must be accessed using the SYSTEM context. If you are using Auto Pilot this will be accessed during the enrollment status part:
https://enterpriseregistration.windows.nethttps://login.microsoftonline.comhttps://device.login.microsoftonline.comhttps://autologon.microsoftazuread-sso.com(If you use or plan to use seamless SSO)
To verify if the device is able to access the above Microsoft resources under the system account, you can use Test Device Registration Connectivity script.
Review AD DS UPN support for Hybrid Azure AD join
The table below provides details on support for on-premises AD UPNs in Windows 10 Hybrid Azure AD join
| Type of on-premises AD UPN | Domain type | Windows 10 version | Description |
|---|---|---|---|
| Routable | Federated | From 1703 release | Generally available |
| Non-routable | Federated | From 1803 release | Generally available |
| Routable | Managed | From 1803 release | Generally available, Azure AD SSPR on Windows lockscreen is not supported |
| Non-routable | Managed | Not supported |
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-plan
Auto Pilot Items
With Hybrid and Auto Pilot you will lose some functionality. You will not be able to do dynamic naming, you can only use a prefix and then intune will add a random string to the end of the prefix. Also devices MUST be able to talk to the local domain environment because it will create the device in AD DS first, during the Enrollment process if it cannot hit your DC it will fail every time.
Configure AD Connect
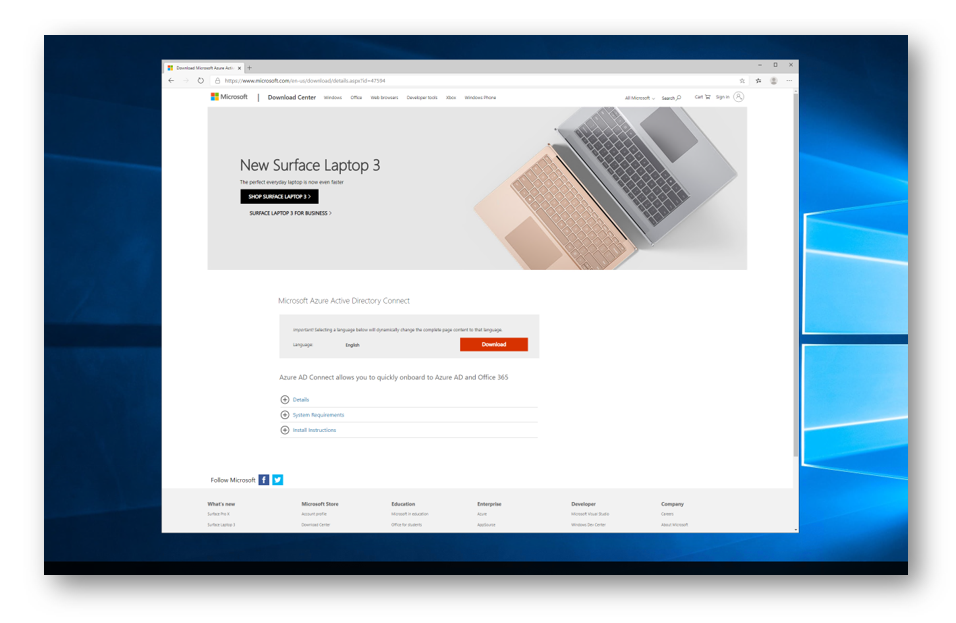
In a hybrid environment you will need to configure AD Sync to sync not only your ADDS users, but also the ADDS devices. These are the users and computers you would see in Active Directory Users and Computers. Download the AD Connect executable from here.
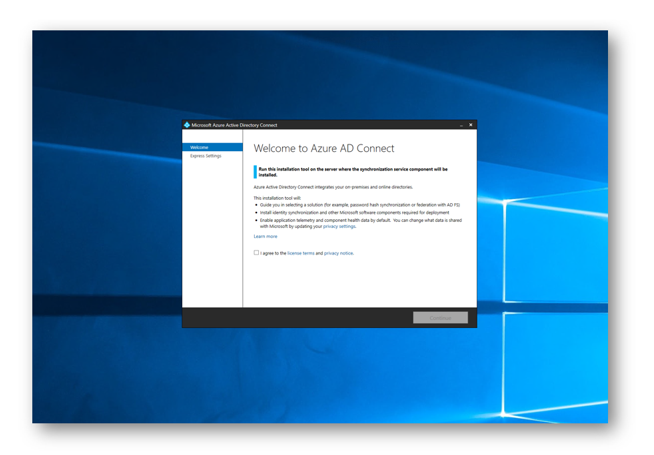
Run the installer and agree to the license terms and privacy notice and then click Continue
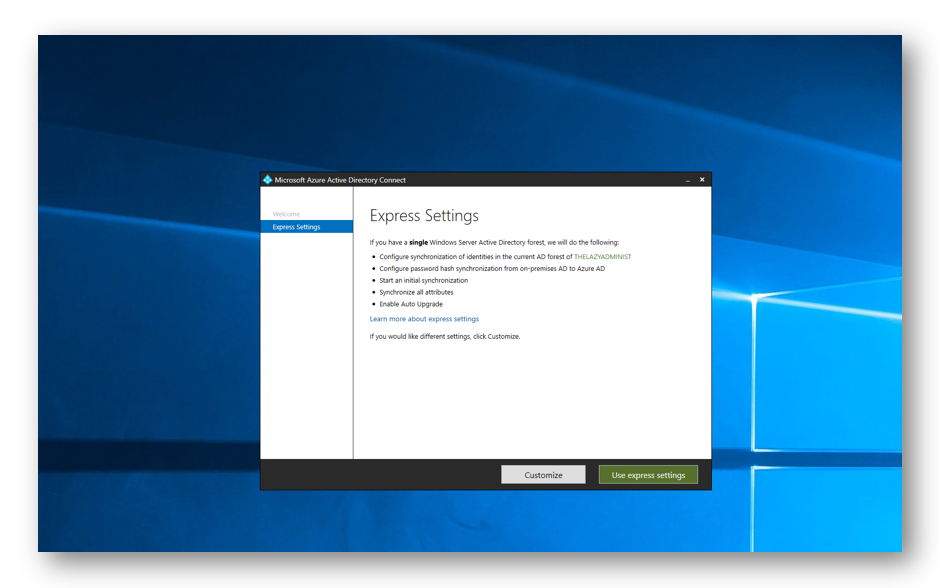
Select Use Express Settings
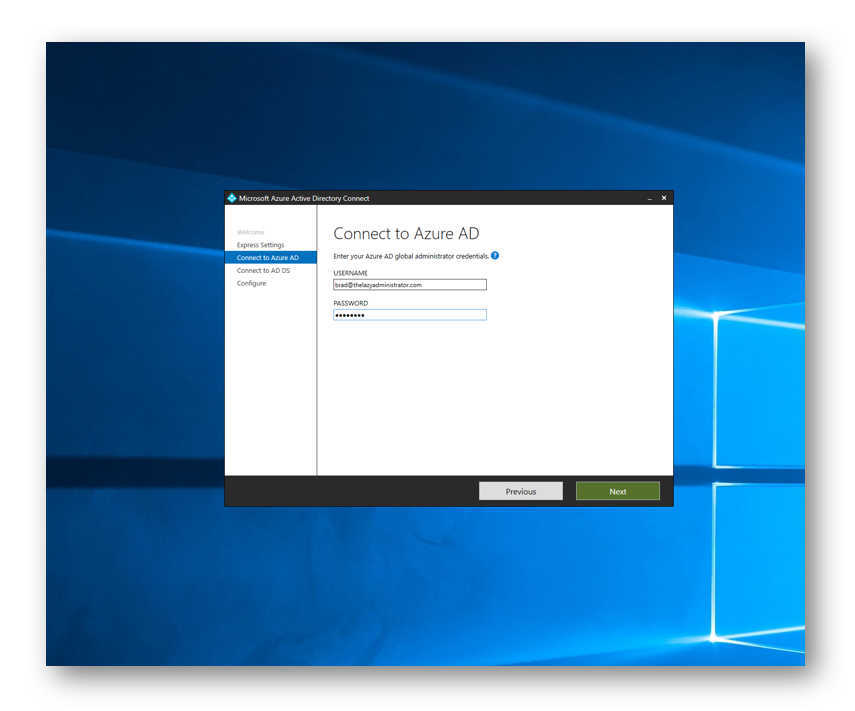
Enter in your Global Administrator credentials to connect to Azure AD
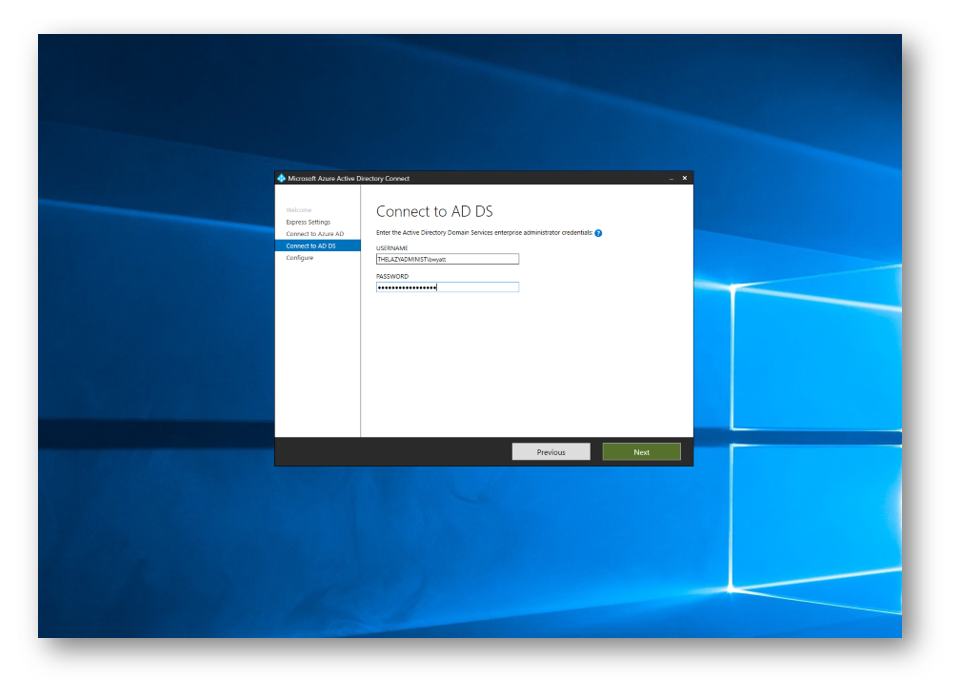
Enter in credentials to connect to AD DS. The account must be a Enterprise Administrator
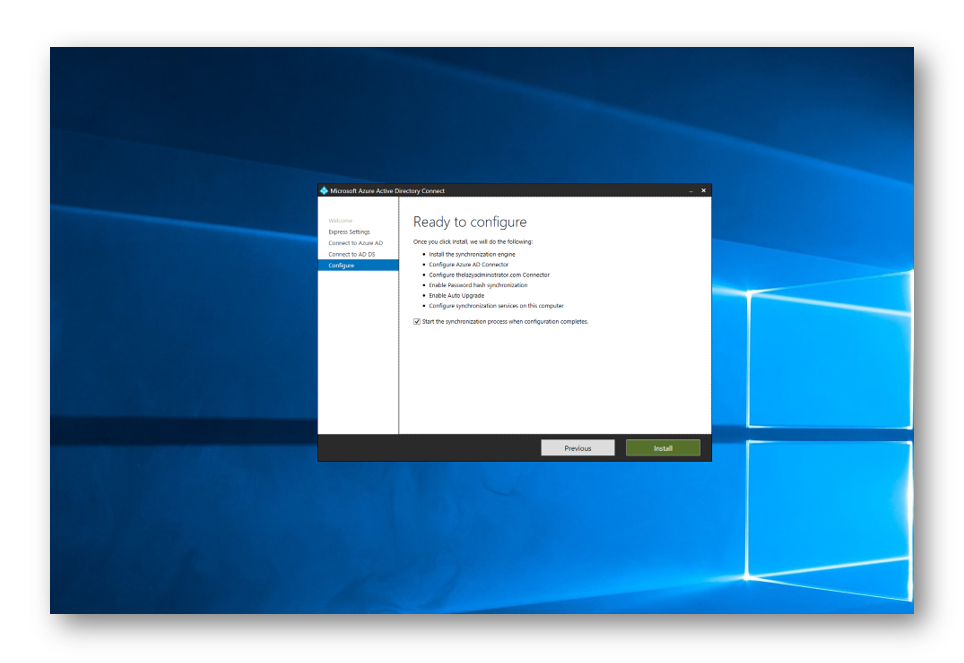
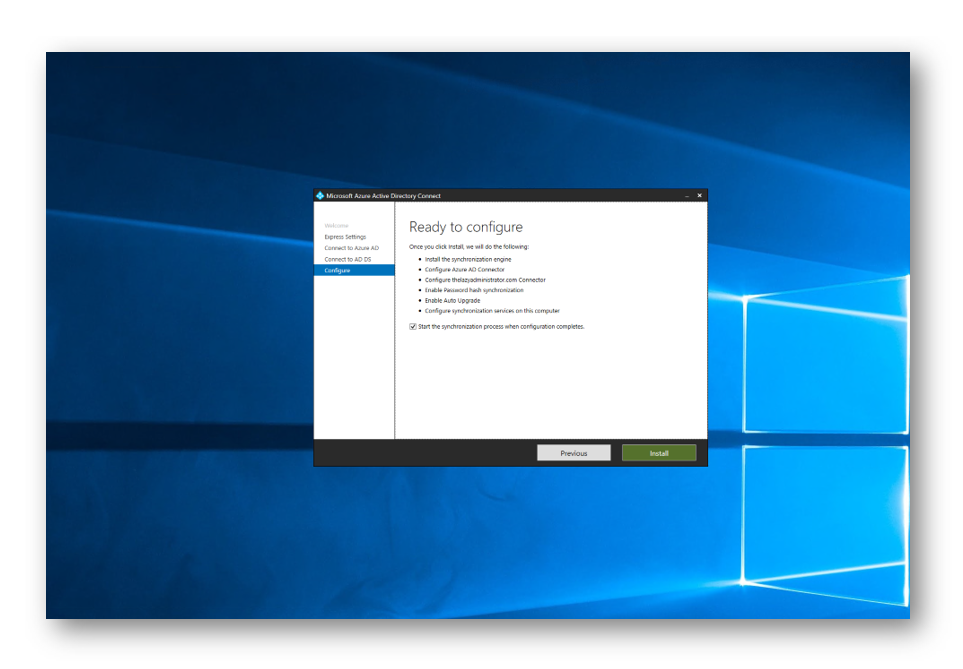
Select Install
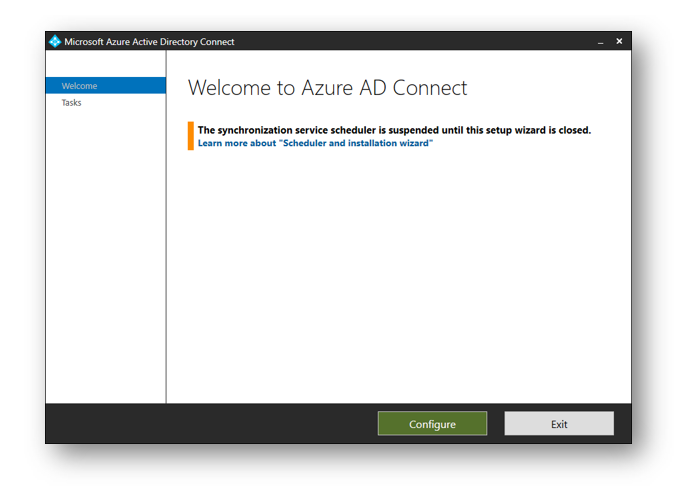
When finished, press Exit
Configure Hybrid Azure AD Join
You will now see an Azure AD Connect icon on your Desktop. Double click the icon as we need to configure Device sync
Click the green Configure button to configure AD Connect
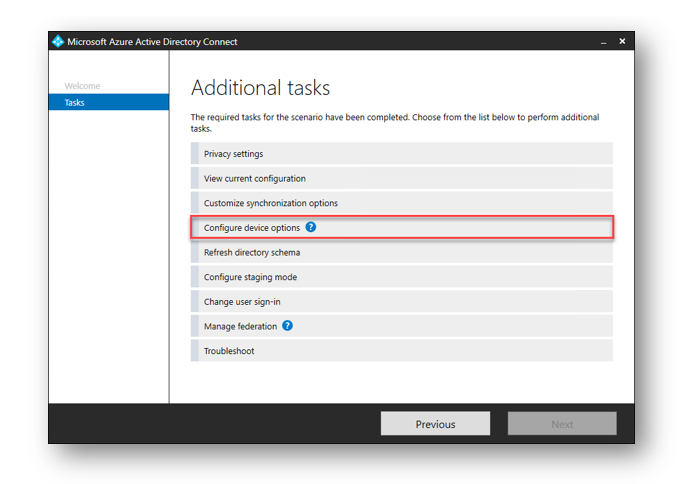
Select Configure Device Options and then click Next
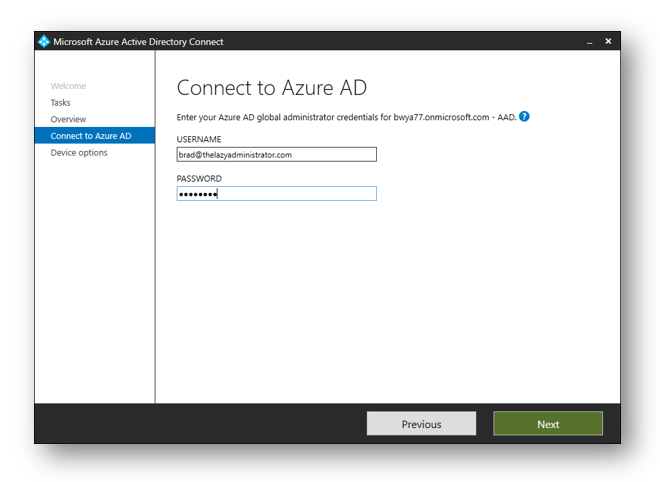
Enter in your global administrator credentials to connect to Azure AD and then click Next
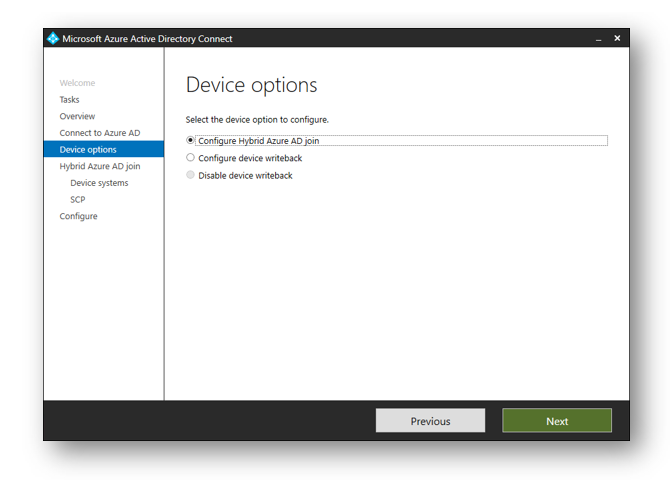
Click the Configure Hybrid Azure AD Join and then click Next
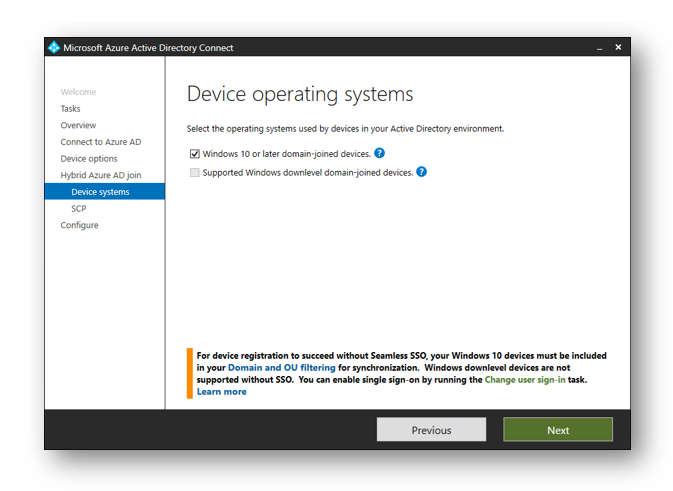
Select Windows 10 or later domain-joined devices and then select Next
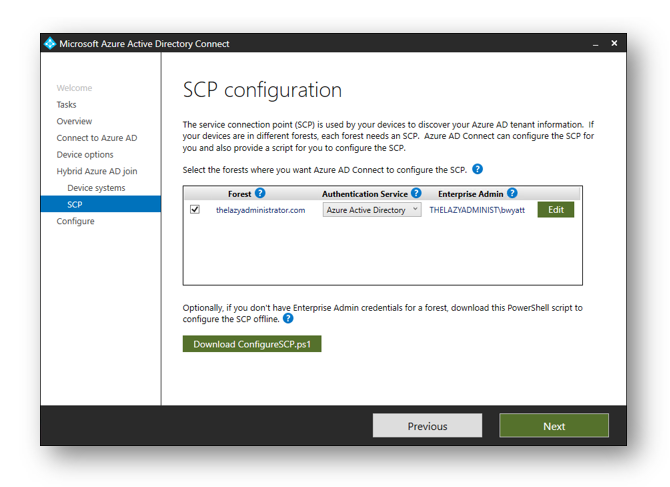
Select your ADDS forest, authentication service and then provide a enterprise administrator
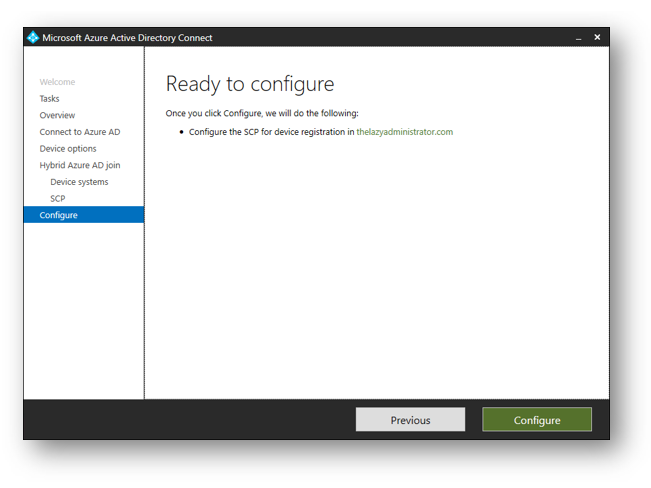
Once you are ready to configure, select Configure
Set up Intune Hybrid Connector
Prerequisites
- The server that will run the Intune Hybrid Connector must be at least running Windows Server 2016
- Must be able to access the internet
- Able to talk to a local domain controller
Install the Intune Connector
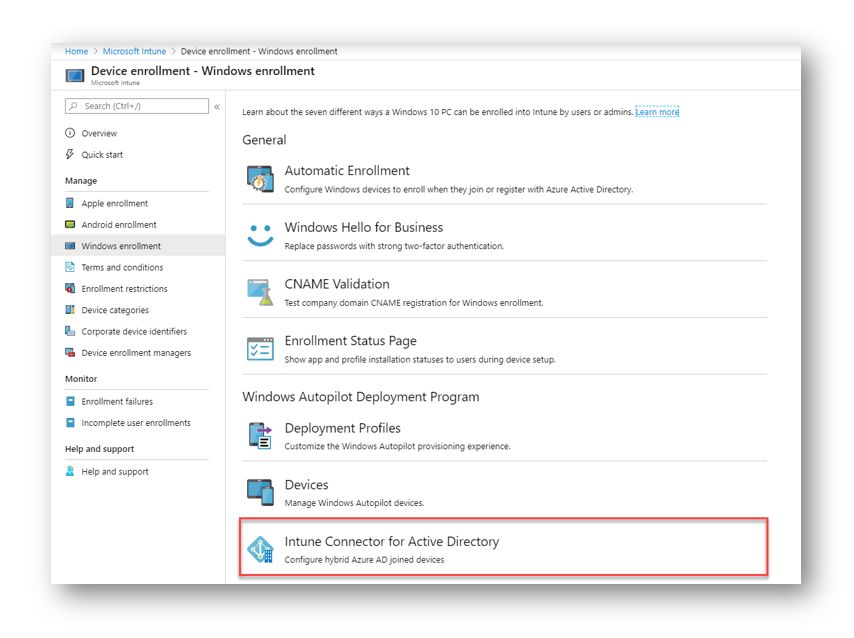
First, download the Intune connector from here or in your Azure portal by going to Device Enrollment > Windows Enrollment > Intune Connect for Active directory
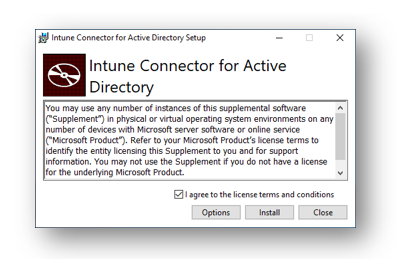
Accept the license terms and conditions and then select Install
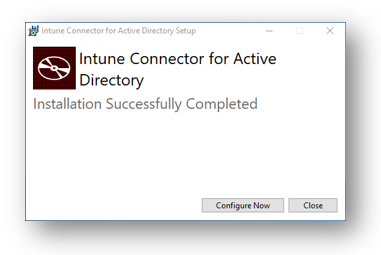
Once it has finished select Configure Now
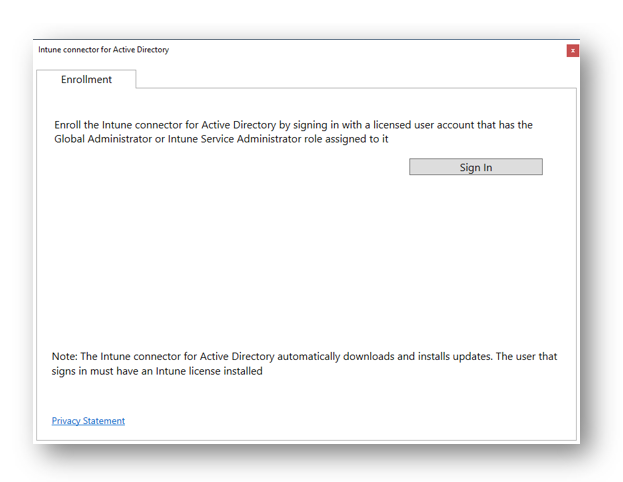
Next, select Sign In
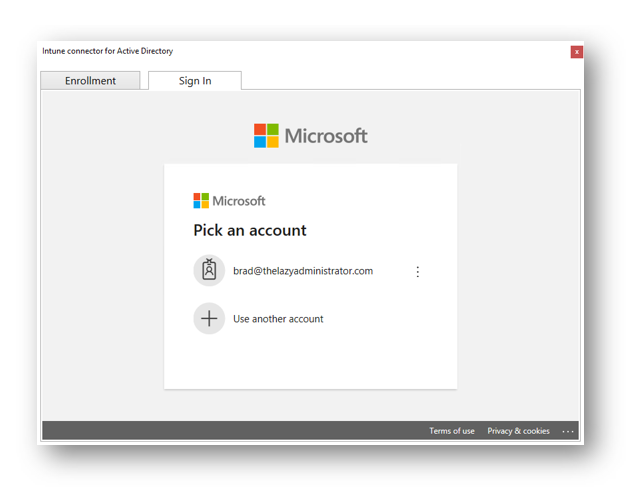
Sign in with an account that has at least a Global Administrator role
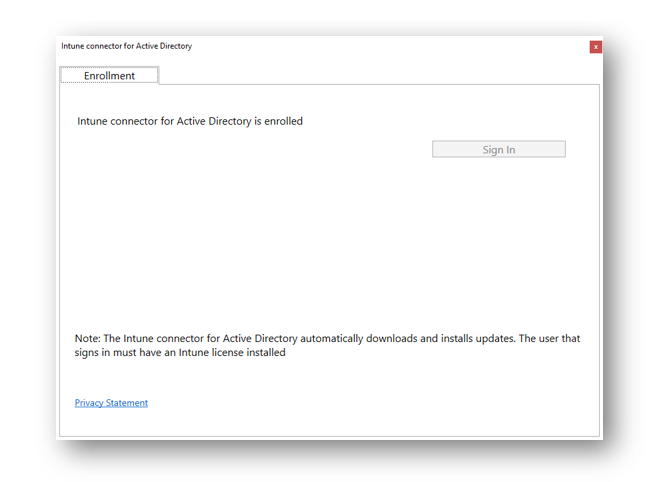
Finally, you will see that the Intune Connector for Active Directory is enrolled
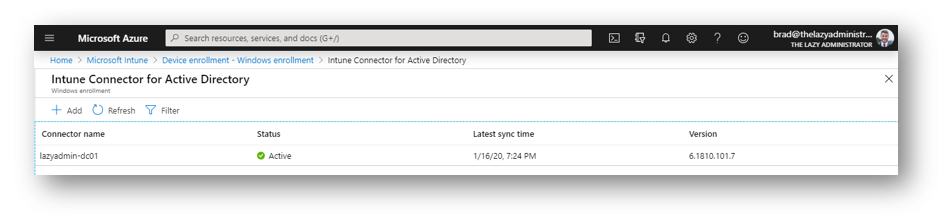
Back in our Azure Portal we can now see our Intune Connector
Configure OU Delegate Control
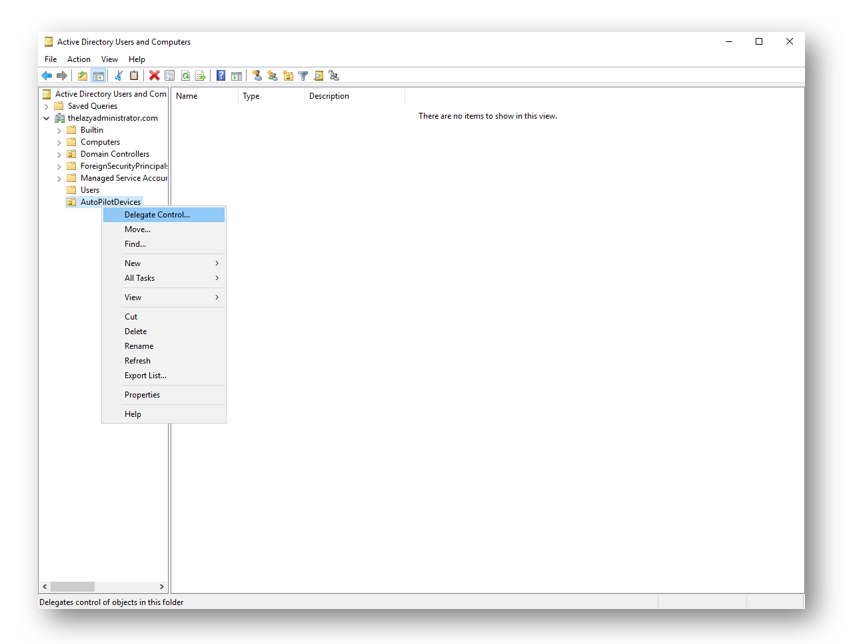
In this step we will need to configure a new Organizational Unit for out hybrid devices, this step is only needed for Auto Pilot since it will be creating devices this OU. If you are just doing Hybrid Azure AD with ADDS you do not need to this step. You do not need a separate OU for your hybrid devices but you will need to configure delegate control. Right click your OU and select Delegate Control
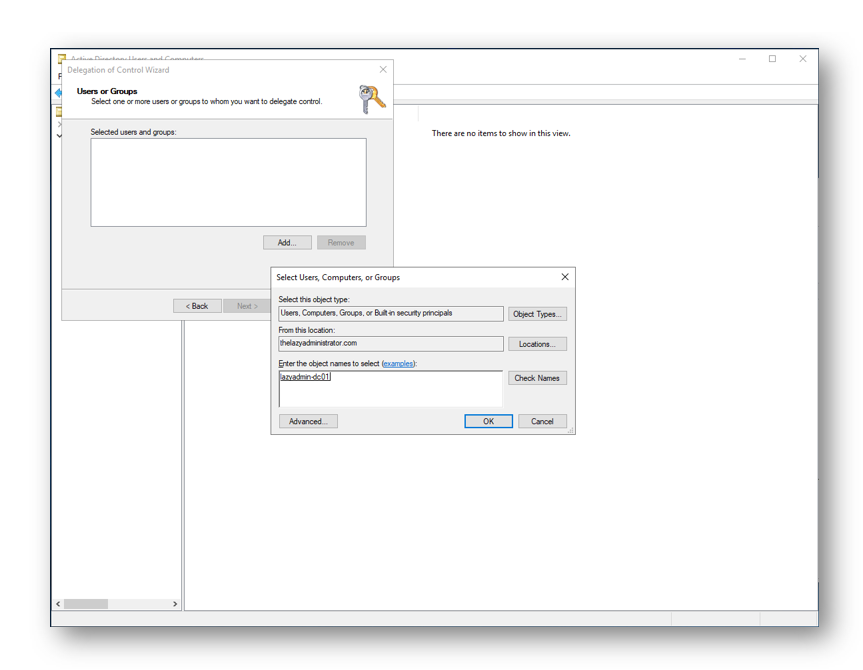
In the Selected users and groups select Add and under Object Types you will want to include computer objects. Add the computer that holds you Intune Hybrid Connector and then Press Next
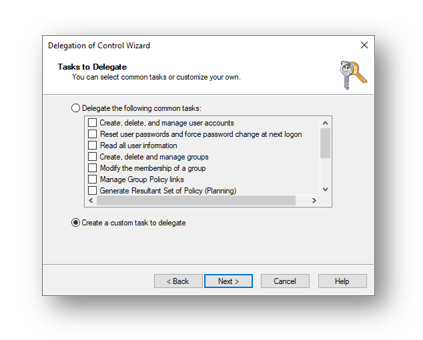
Select Create a custom task to delegate and then press Next
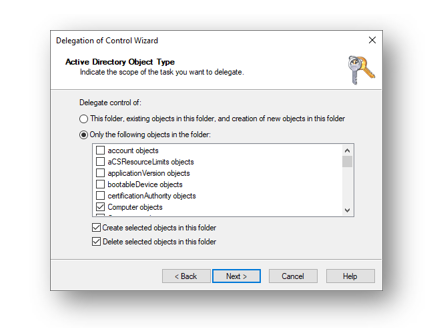
In the next pane, select Computer Object under Only the following objects in the folder, then select the Create selected objects in this folder and Delete selected objects in this folder checkboxes.
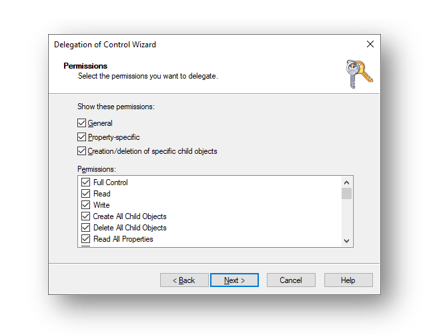
Check General, Property-Specific, Creation/deletion of specific child objects and Full Control
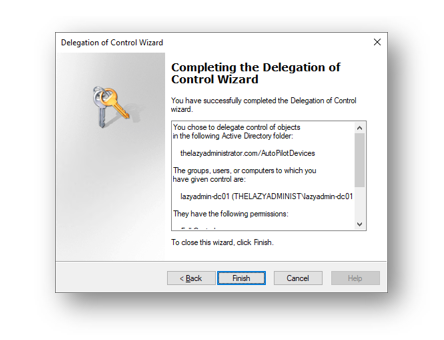
Finally select Finish
Intune Hybrid Domain Join Configuration Profile
Next, we must create a Intune Configuration profile to tell our devices to hybrid domain join.
In Intune go to Device Configuration > Profiles > Device Profiles and then Add Profile.
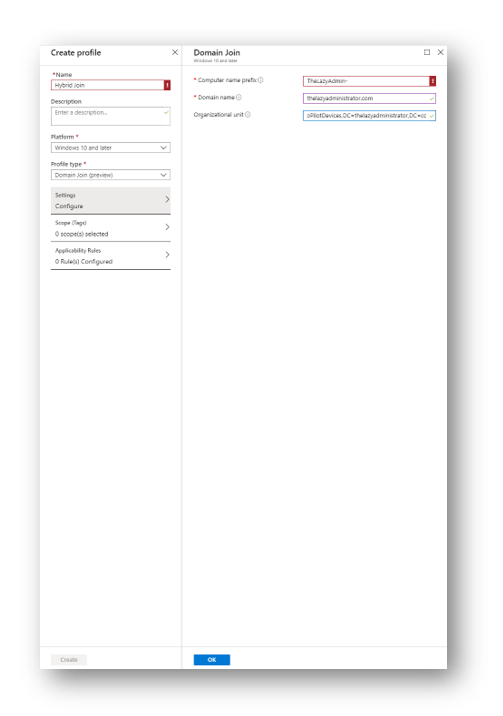
Give your profile a name, select the platform as Windows 10 or later and the profile type to Domain Join. Enter a computer name prefix, the domain name and the OU in Distinguished name format.
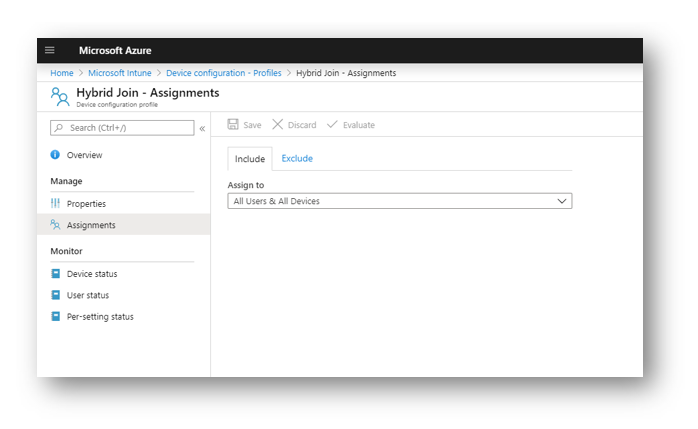
Next you must assign the policy to users or devices. In my tenant I select all users and devices
Auto Pilot Hybrid Deployment Profile
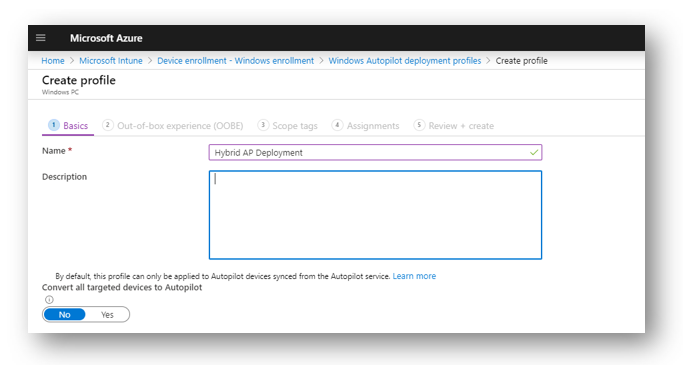
Now we must create an Auto Pilot Hybrid deployment profile. In Azure go to Intune > Device Enrollment > Windows Enrollment > Deployment Profiles and select Create Profile
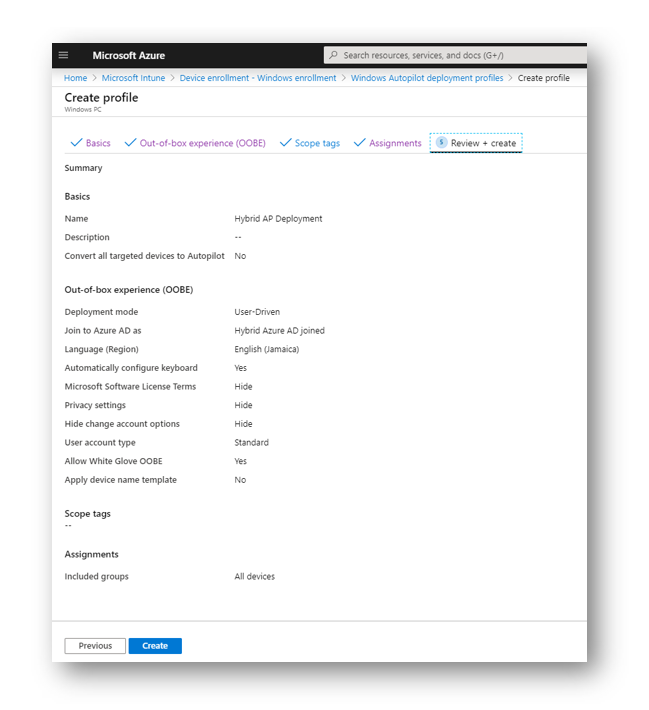
Give your new deployment profile a name and description then press Next
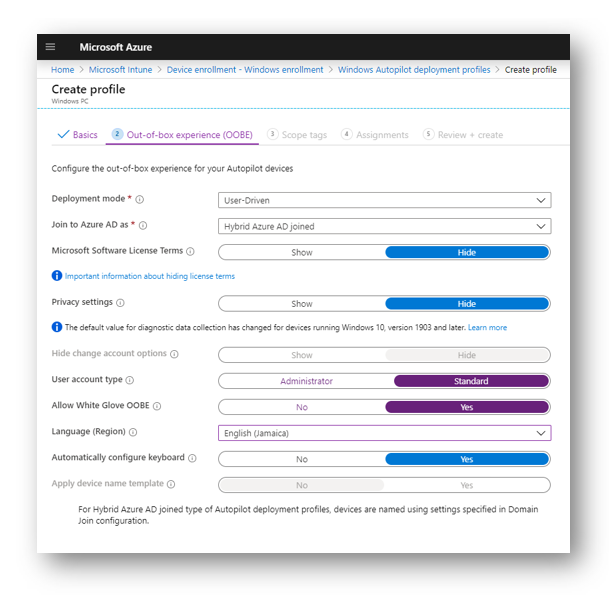
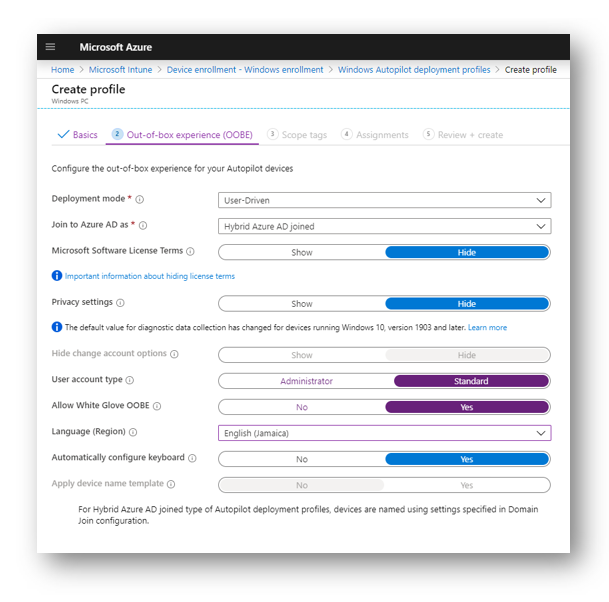
Configure your Out of Box exerpeience to your standards. You MUST select join to azure AD as and select Hybris Azure AD Joined
Select your group assignments. Some people may apply it to an Auto Pilot only device group, some may do static groups (have groups for non hybrid and hybrid) In my test tenant I select all devices
When you are finished you can press Create
Disable User ESP
In a Auto pilot Hybrid Domain Join scenario, you may observe an error in enrollment status page (ESP). This error is because of the timeout as mentioned in Michael Niehaus post.
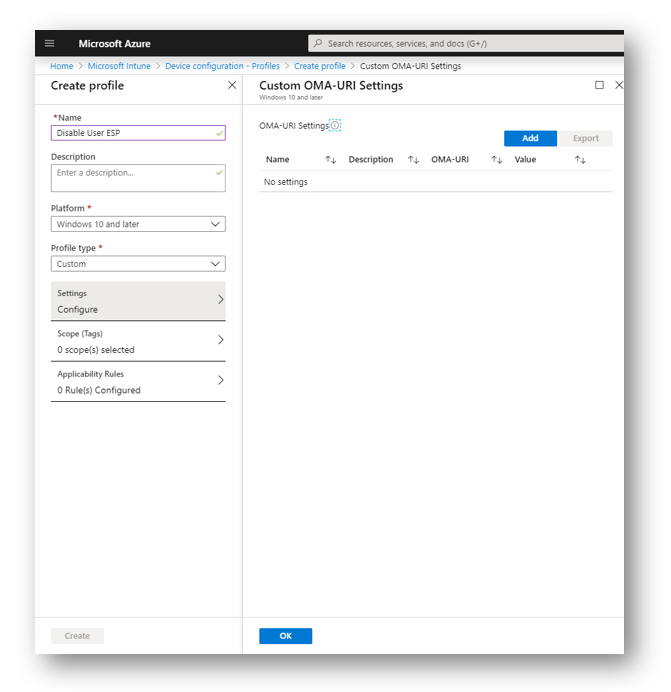
In the Azure Portal go to Intune > Device Configuration > Profiles > Create Profile
Give the profile a Name, select Windows 10 and later for platform and then profile type is Custom
Add the following items:
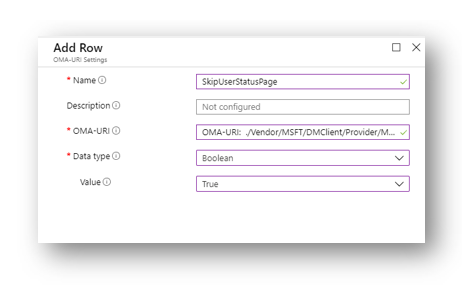
Name: SkipUserStatusPage (or whatever you want) OMA-URI: ./Vendor/MSFT/DMClient/Provider/MS DM Server/FirstSyncStatus/SkipUserStatusPage Data type: Boolean Value: True
And then under Assignments assign it to devices or users
Results
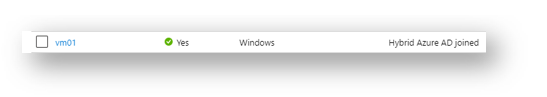
Once I have all this set up I tested with a new machine and ran it thought auto pilot. In the Azure AD Devices blade I can see my machine is listed as Hybrid Joined
On the client machine you can go to Settings > Accounts > Access Work and School and see both Azure AD connection as well as AD DS
You can also go to the domain controller where you specified your OU above and see your new device.
Additional Resources

My name is Bradley Wyatt; I am a 5x Microsoft Most Valuable Professional (MVP) in Microsoft Azure and Microsoft 365. I have given talks at many different conferences, user groups, and companies throughout the United States, ranging from PowerShell to DevOps Security best practices, and I am the 2022 North American Outstanding Contribution to the Microsoft Community winner.

3 thoughts on “Configure Autopilot Hybrid Azure-AD and ADDS Domain Join”
Hi does a hybrid joined device need to have continuous connectivity to the on-prem domain controller? Or does it just join Azure AD and the user can login as their on-prem AD account synced password?
it does not have to have continuous connectivity – just for the initial domain join process and every 30 days or so so it doesn’t lose trust