Windows LAPS Management, Configuration and Troubleshooting Using Microsoft Intune
Table of Contents
Windows Local Administrator Password Solution (Windows LAPS) is a Windows Feature that allows IT Administrators to secure and protect local administrator passwords. This includes automatic rotation of passwords as well as backing up the passwords to Azure Active Directory or Active Directory. You can configure Windows LAPS on your Windows endpoints using Microsoft Intune.
Pre-requisites
To use Windows LAPS in Intune, ensure you’re using a supported Windows platform:
- Windows 10 20H2 and later with April 11, 2023 security updates installed
- Windows 11 21H2 and later with April 11, 2023 security updates installed
- Windows Server 2019 and later with April 11, 2023 security updates installed
You might also have to enable Azure AD Local Administrator Password Solution (LAPS) within your Azure Tenant.
- Azure Active Directory > Devices > Device Settings > Azure AD Local Administrator Password Solution (LAPS)
Note: You may not have to do this once the product is out of Public Preview.
Configure LAPS with Intune
Create Account Protection Policy
In the Microsoft Intune Portal (Intune.Microsoft.com) go to Endpoint Security > Account Protection and click + Create Policy
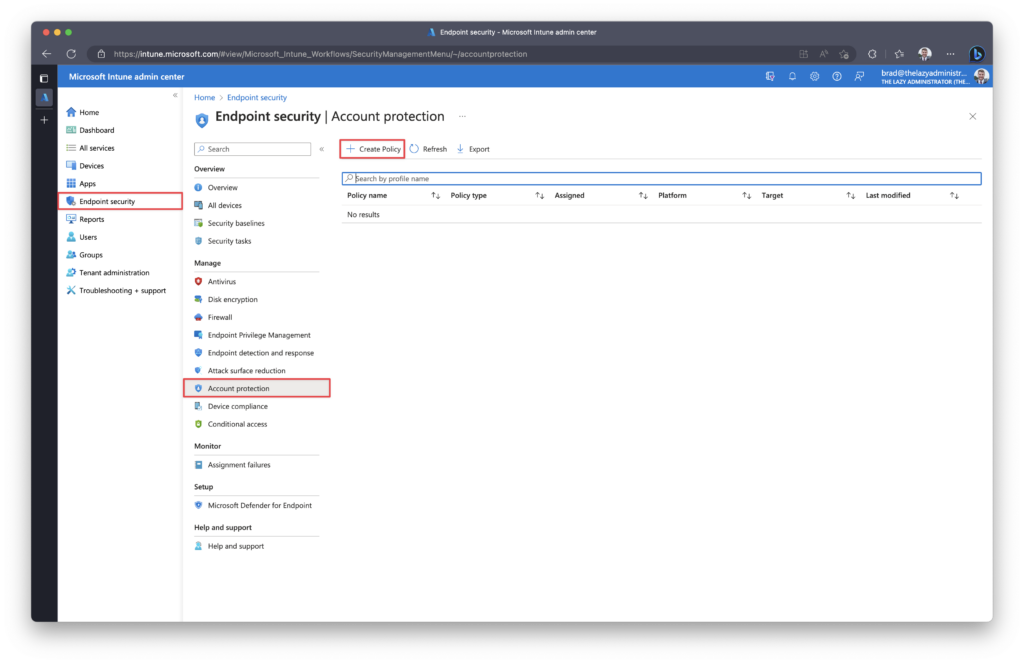
For Platform select, “Windows 10 or later” and for Profile select, “Local admin password solution (Windows LAPS)”
Once completed, click Create
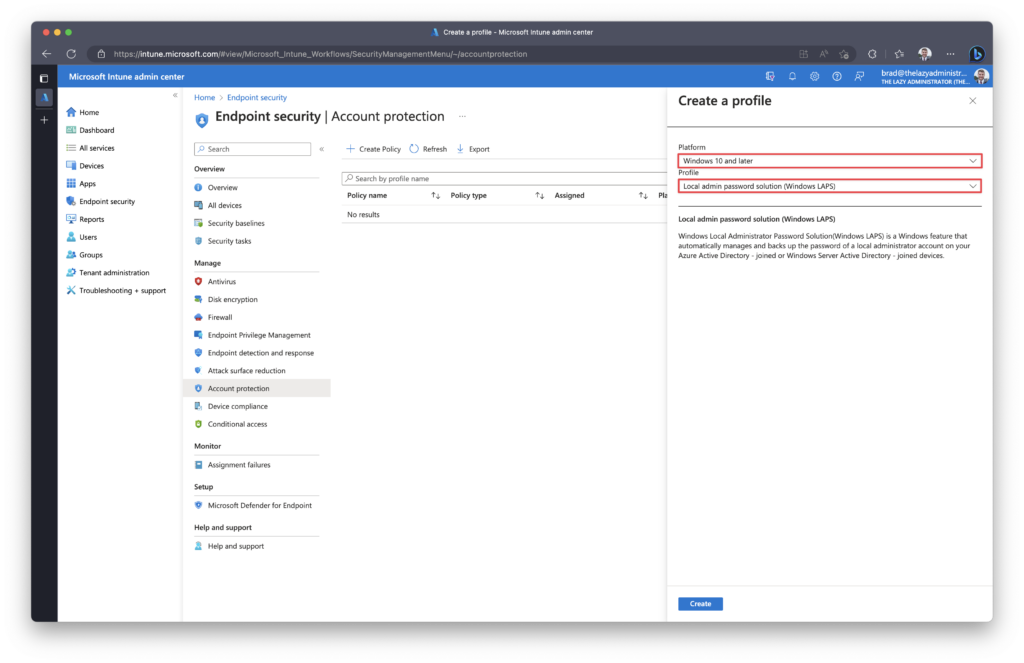
Give your new policy a proper name and description (optional) and then click Next
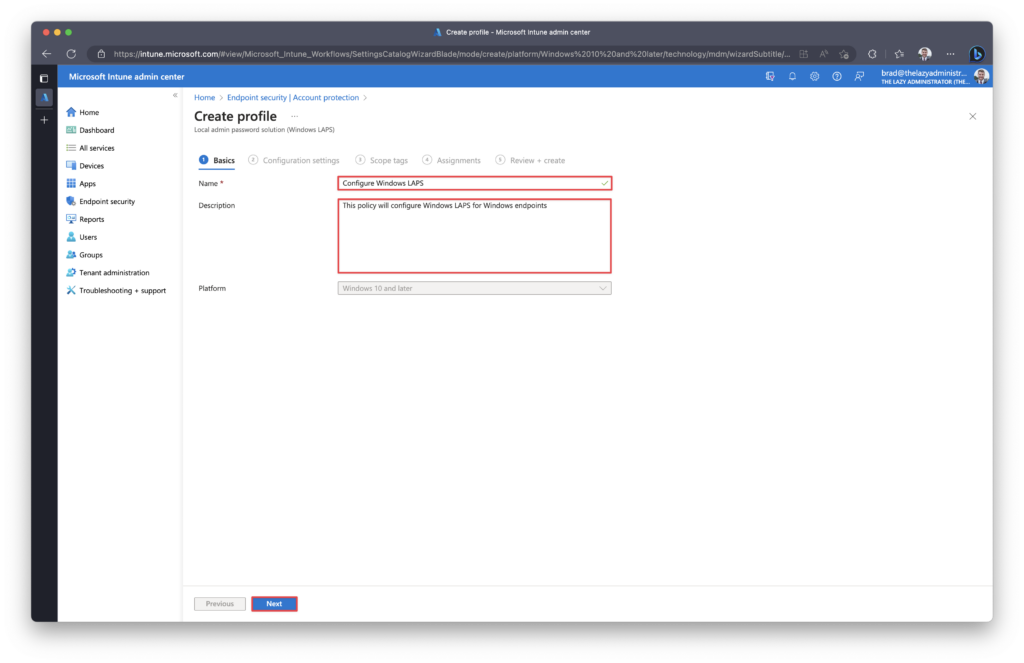
Configuration Settings
Below I will review the different configuration options that are available. Microsoft also maintains documentation for all settings here.
Backup Directory: Allows you to backup the Local Administrator password to Azure Active Directory or Active Directory.
Administrator Account Name: If configured, the specified account’s password will be managed via the policy. If not specified, the default built-in local administrator account will be located by well-known SID (even if it has been renamed)
Note: if a custom managed local administrator account name is specified in this setting, that account must be created via other means. Specifying a name in this setting will not cause the account to be created.
Password Complexity: Allows an IT admin to configure password complexity of the managed local administrator account.
Password Length: Configure the length of the password. By default the value is 14, the minimum value is 8 and maximum value is 64.
Post Authentication Actions: This setting specifies what LAPS should do with the account after a successful authentication. By default it will log off the managed account and reset the password.
Post Authentication Reset Delay: How long it will wait until it performs the Post Authentication Action that we specified above. Default is 24 hours.
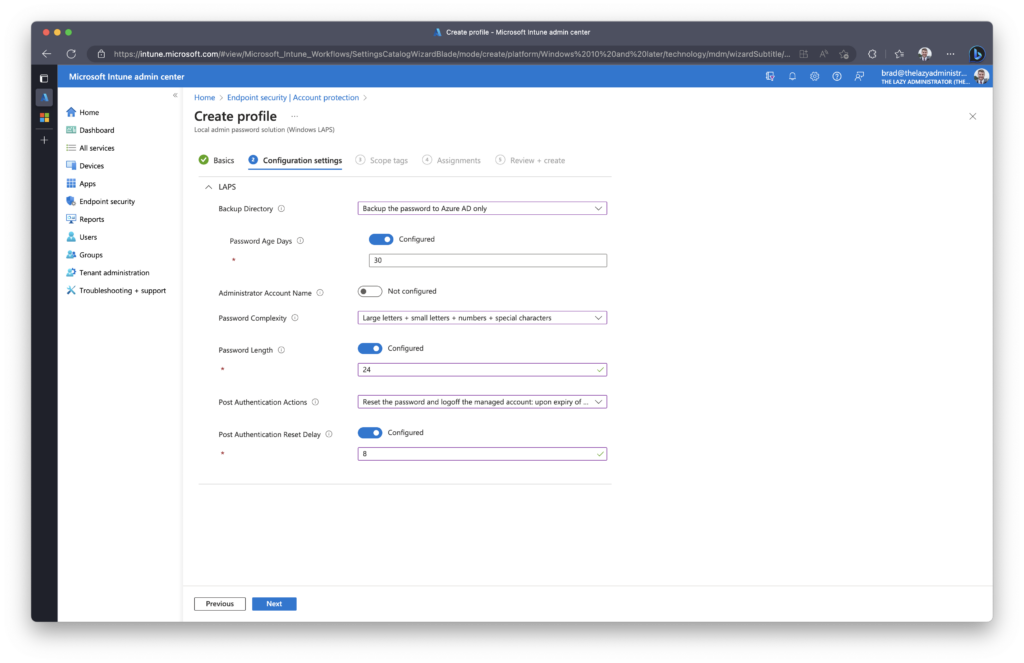
In the Assignments tab, assign the new policy to a device group, or all devices.
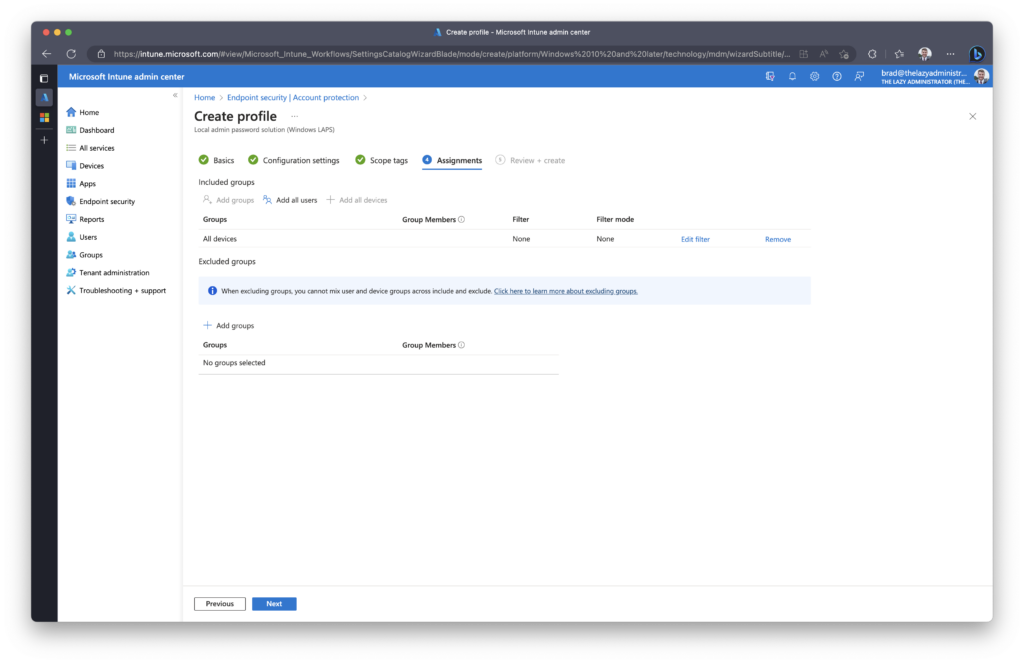
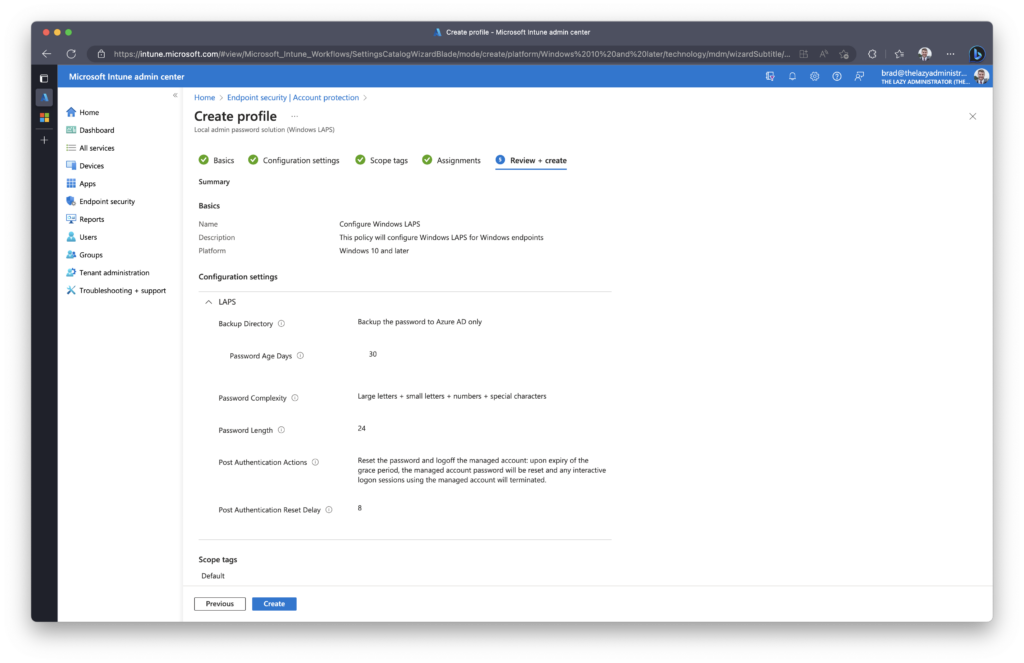
In the Review + Create pane, verify the policy meets your requirements prior to finishing.
Viewing a Device’s Local Admin Password
There are several ways an IT administrator can view an endpoints local administrator password, from the Intune Admin Portal, Microsoft Entra, to even using PowerShell.
Microsoft Entra
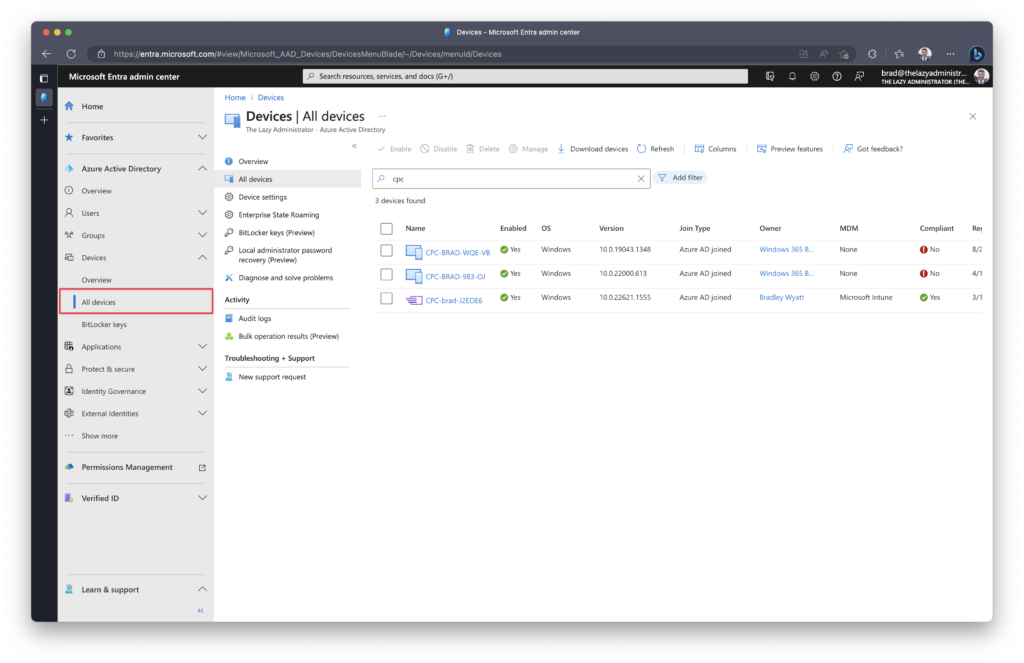
First, navigate to the Microsoft Entra admin portal here.
On the left pane under Azure Active Directory > Devices > click All Devices
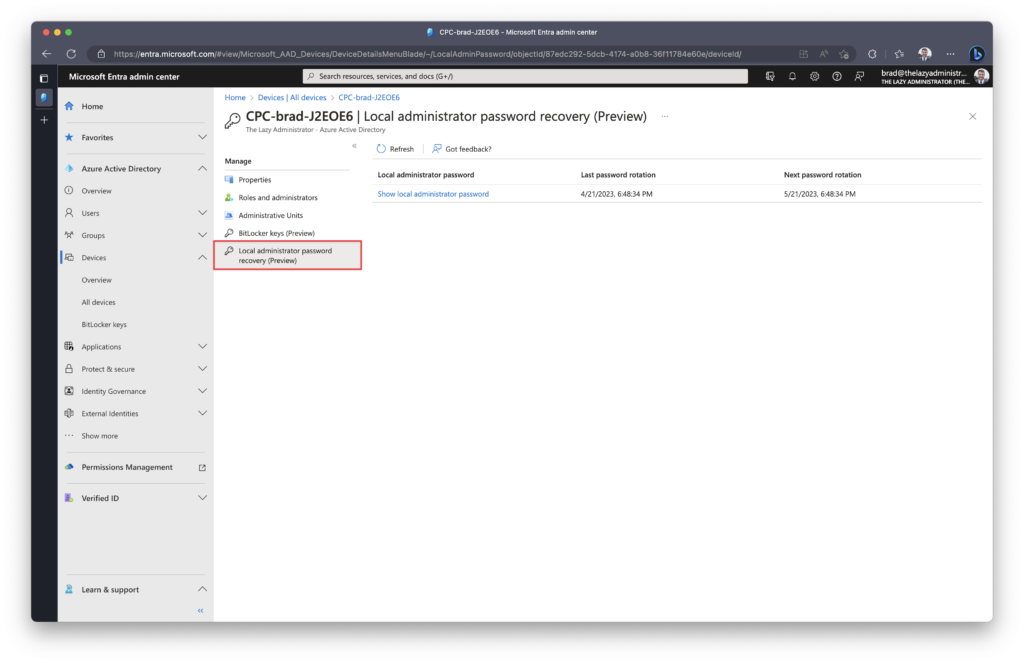
On the left pane you can select Local Administrator Password Recovery and from there show the administrator password.
Intune Portal
Navigate to the Intune Portal at intune.microsoft.com and go to Devices and then select your device. On the left Pane you will see Local admin password.
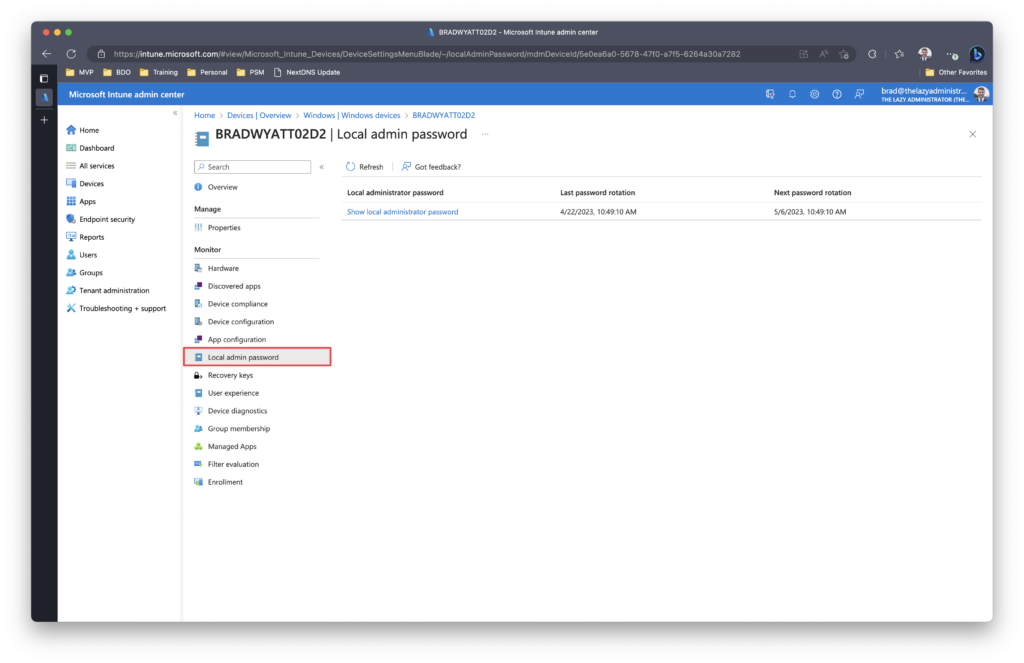
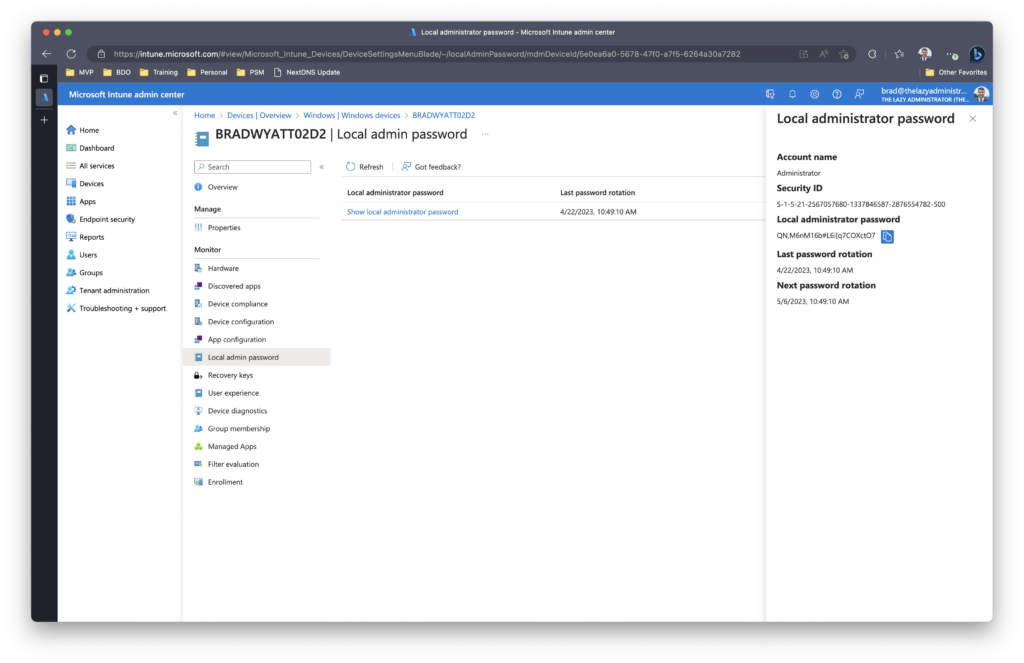
Next, you can click to view the local administrator password.
Note: If admins don’t have the correct permissions, they won’t be able to view the relevant information. This information is controlled by the deviceLocalCredentials.Read.All permissions that are specific to Global Admin, Cloud Device Admin, and Intune Admin, which only allows them to recover the Windows LAPS password.
PowerShell
Install the PowerShell Modules
First, Install the Microsoft Graph SDK
Install-Module Microsoft.Graph -Scope AllUsersNext, install the Az module
Install-Module Az -Scope AllUsersCreate an Azure Active Directory registered app to retrieve Windows LAPS passwords
Using the Az module, connect to Azure by running Connect-AzAccount
Connect-AzAccountNext, we need to create the Azure AD registered application. Using the PowerShell code below, we can create a new application called IntuneLAPSadmin.
$AppRegistrationSplat = @{
DisplayName = "IntuneLAPSadmin"
}
$AzureADApp = New-AzADApplication @AppRegistrationSplat Next, we need to grant the proper permissions to our newly created Application. The application must have the Device.Read.All permission and then one of the following two, DeviceLocalCredential.Read.All or DeviceLocalCredential.Read.All.
- Use
DeviceLocalCredential.ReadBasic.Allto grant permissions for reading non-sensitive metadata about persisted Windows LAPS passwords. Examples include the time the password was backed up to Azure and the expected expiration time of a password. This permissions level is appropriate for reporting and compliance applications. - Use
DeviceLocalCredential.Read.Allto grant full permissions for reading everything about persisted Windows LAPS passwords, including the clear-text passwords themselves. This permissions level is sensitive and should be used carefully.
The table below will list the permission and its corresponding permission ID. Take note of the permission ID for the next step.
| Permission | ID |
| Device.Read.All | 7438b122-aefc-4978-80ed-43db9fcc7715 |
| DeviceLocalCredential.Read.All | 884b599e-4d48-43a5-ba94-15c414d00588 |
| DeviceLocalCredential.ReadBasic.All | db51be59-e728-414b-b800-e0f010df1a79 |
$AppPermissions = @(
"7438b122-aefc-4978-80ed-43db9fcc7715"
"884b599e-4d48-43a5-ba94-15c414d00588"
)
$AppPermissions | ForEach-Object {
Add-AzADAppPermission -ObjectId $AzureADApp.id -ApiId '00000003-0000-0000-c000-000000000000' -PermissionId $_ -Type Role
}Note: In my example above I am using the DeviceLocalCredential.Read.All permission. Ensure that you choose the correct permission.
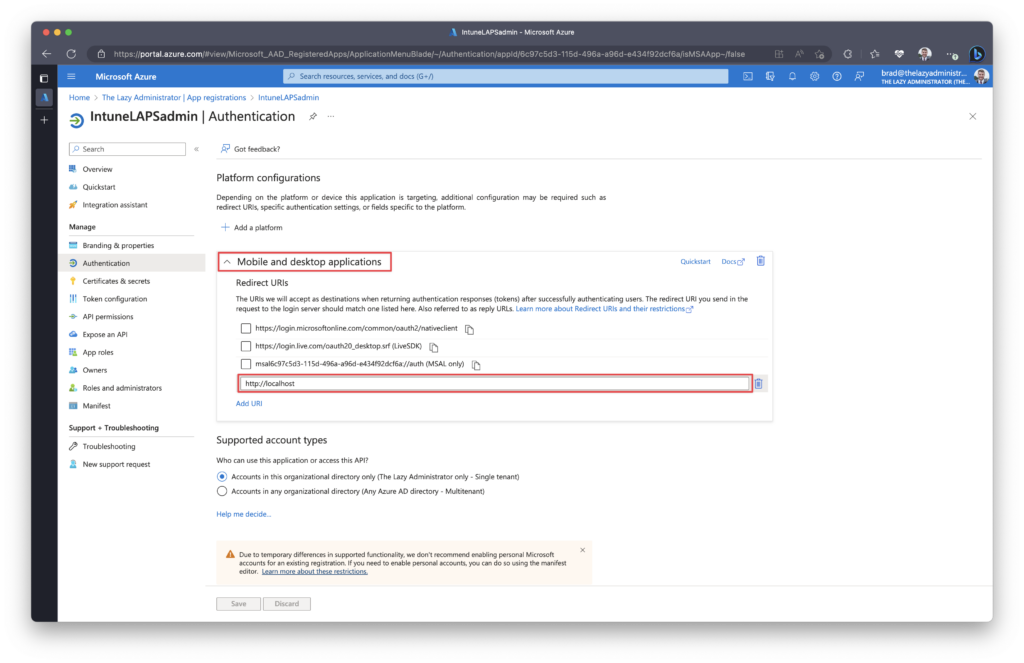
In the Azure Portal, we need to create a Redirect URI for Mobile and desktop applications. This is done in the Azure Portal to Active Directory > App Registrations > [ Your Newly Created Application ] > Authentication and add a custom redirect URI of ‘http://localhost’.
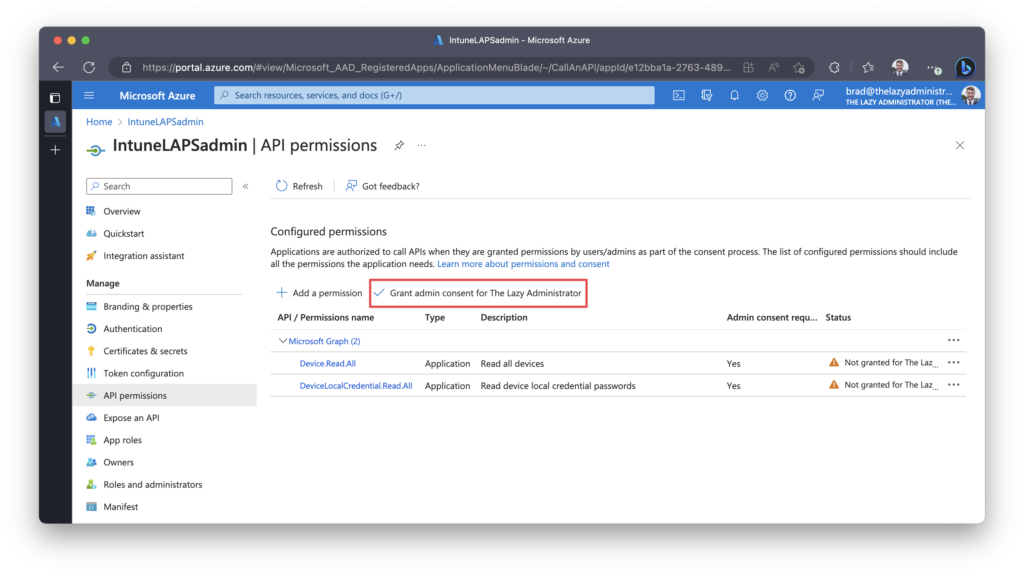
Finally, grant admin consent for the permissions. For this you must go to the Azure Portal to Active Directory > App Registrations > [ Your Newly Created Application ] > API Permissions.
Retrieve Password
First we need to get two items, the ClientID of our application and our tenantID.
ClientID: Azure Portal to Active Directory > App Registrations > [ Your Newly Created Application ]
TenantID: Either use this website, or go to the Azure Portal > Azure Active Directory
Next, using PowerShell and the information gathered above, sign into Microsoft Graph
Connect-MgGraph -Environment Global -TenantId 6438b2c9-54e9-4fce-9851-f00c24b5dc1f -ClientId e12bba1a-2763-4899-9e67-e434f92dcf6a -Scopes "Device.Read.All","DeviceLocalCredential.Read.All"Note: If you granted the permission ‘DeviceLocalCredential.ReadBasic.All’ and not ‘DeviceLocalCredential.Read.All’ then replace the scope with ‘DeviceLocalCredential.ReadBasic.All’
When logging into the first time, you may need to accept the permission prompt.
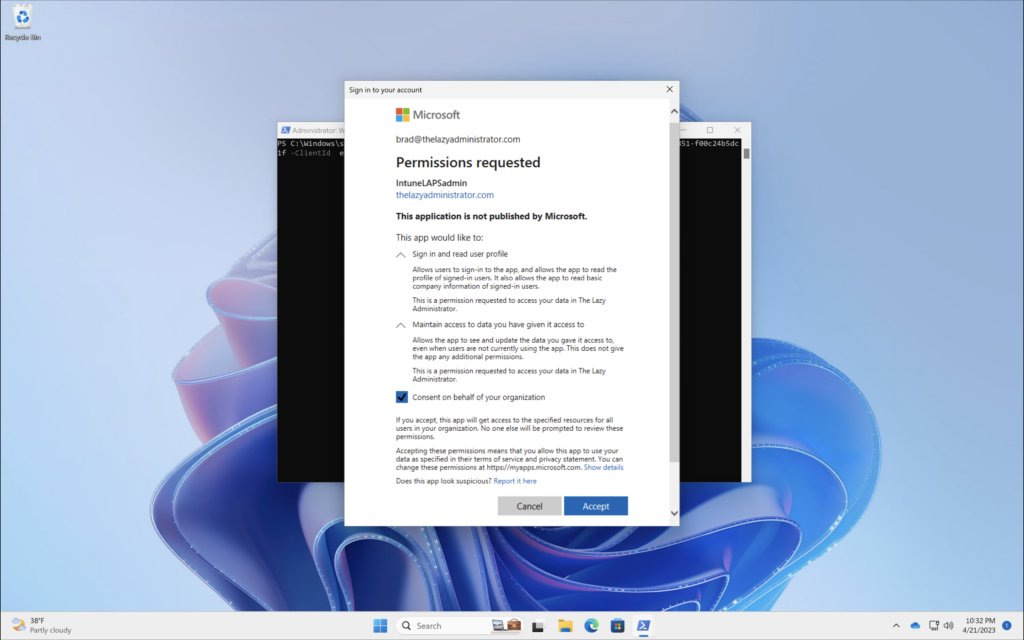
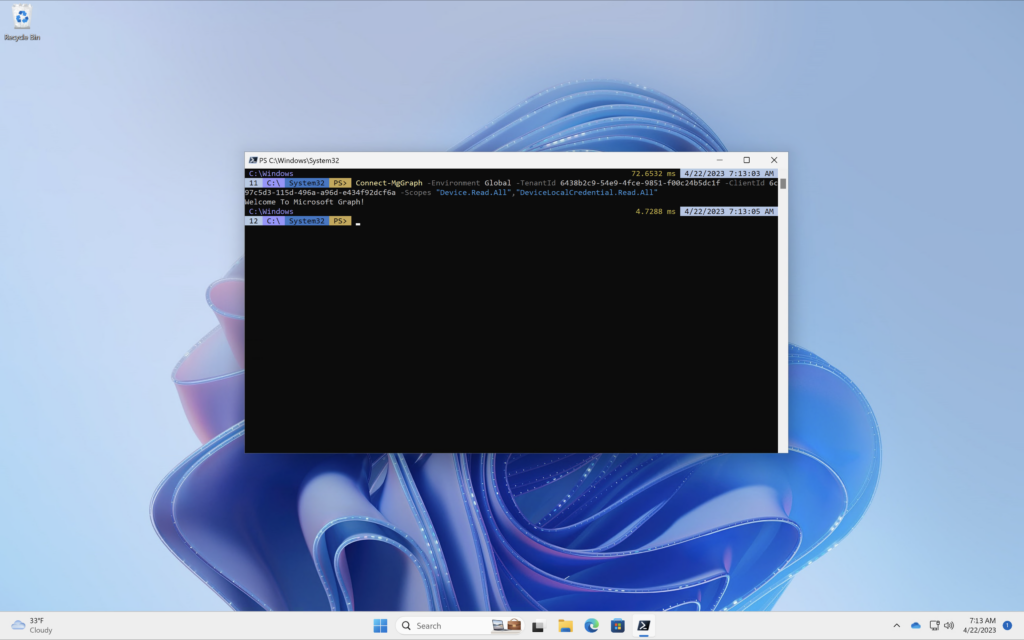
Once it has authenticated you will be presented with a welcome message welcoming you to the Microsoft Graph API.
To get the LAPS password information of a device you will need the device ID (found in the Azure AD Portal). Once you have the device ID, run the following command
Get-LapsAADPassword -DeviceIds 8155b933-9cfa-4d86-ba50-dd72ca6579db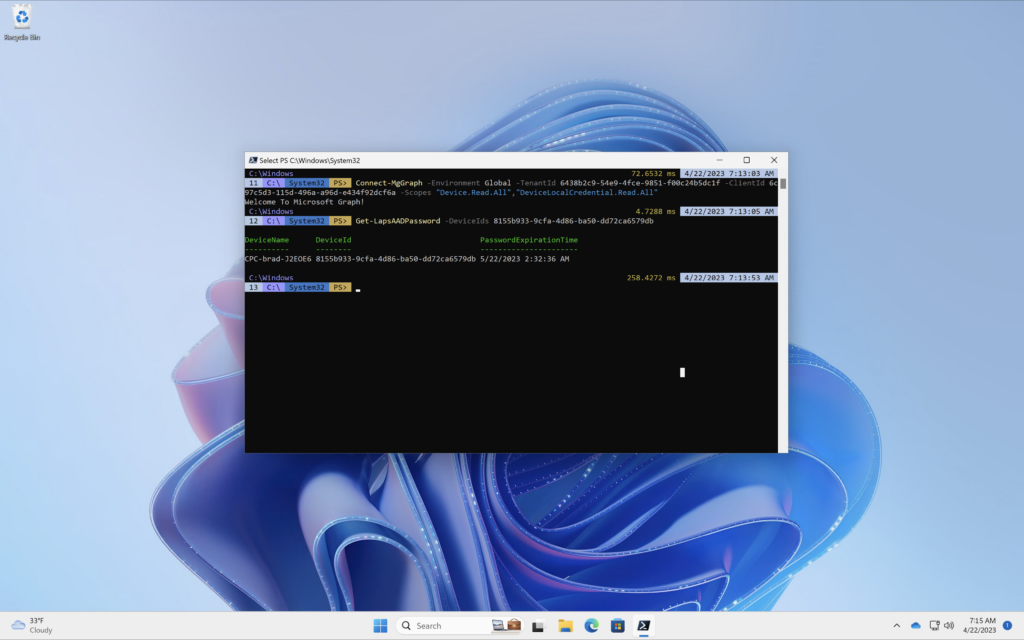
Notice how the information returned does not include the device password. If you granted the permission ‘DeviceLocalCredential.Read.All’ you can run the following command to include the LAPS password for the device.
Get-LapsAADPassword -DeviceIds 8155b933-9cfa-4d86-ba50-dd72ca6579db -IncludePasswords -AsPlainText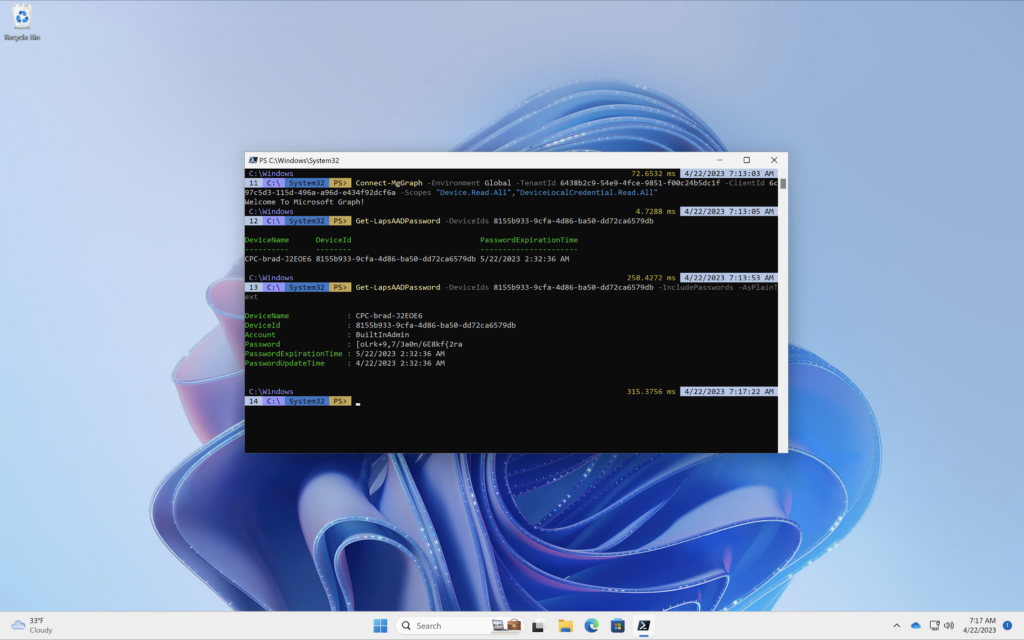
Rotate Passwords
Intune Portal
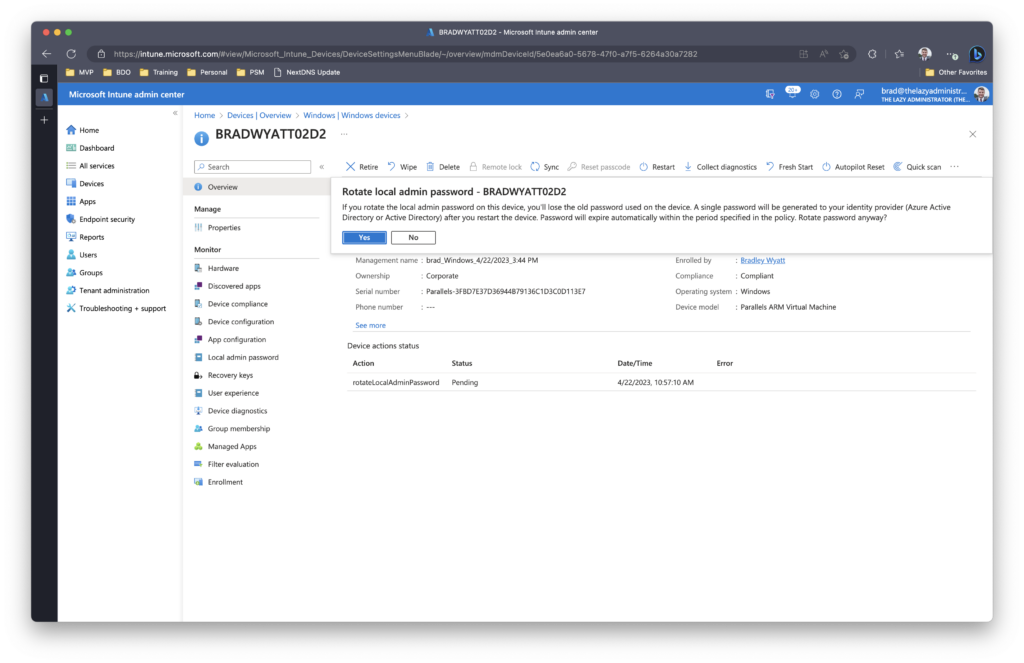
In the Intune Portal, click the device and then click the ellipses in the device overview. From there click Rotate local admin password.
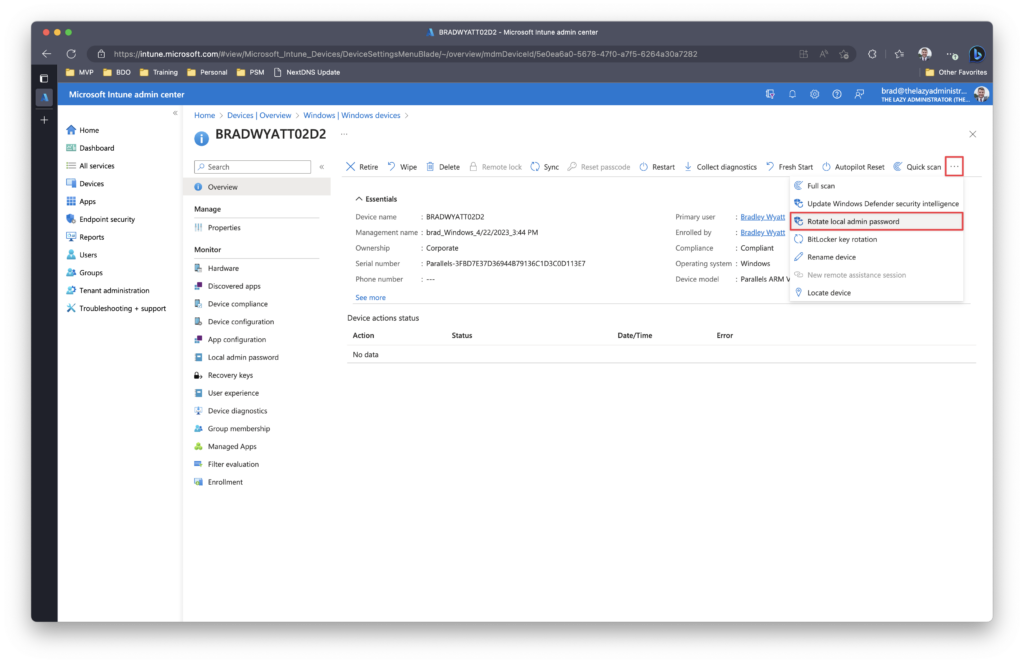
Once the endpoint reboots, the password will be changed.
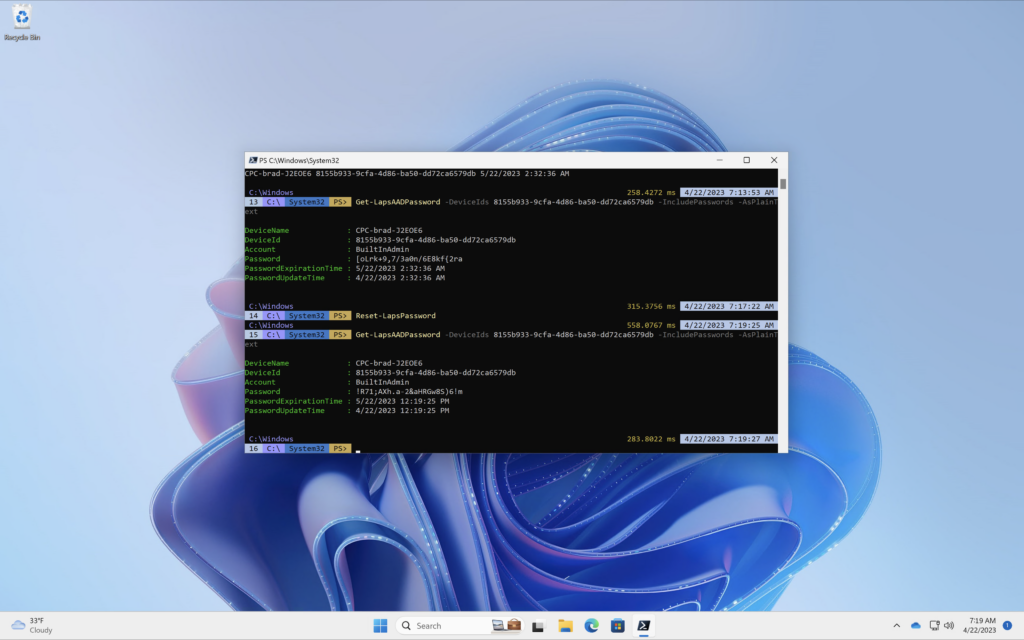
PowerShell
The cmdlet Reset-LapsPassword is ran locally against a machine that is using Windows LAPS. In the example below I am viewing my devices password before and after a rotation to show that it quickly and easily rotated the password.
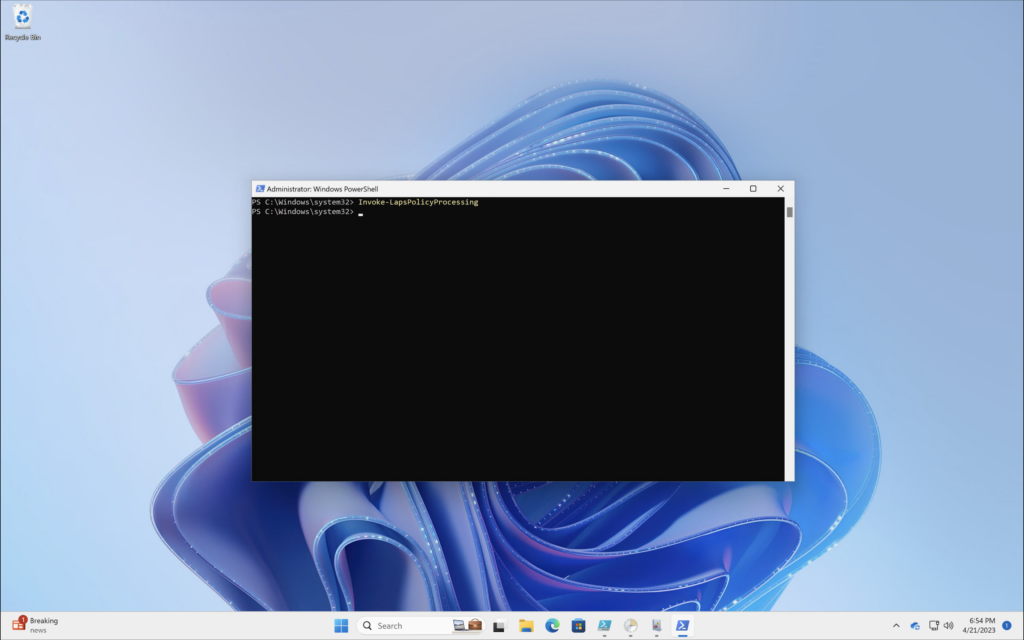
Manually Force Policy Processing
Windows LAPS processes the currently active policy on a periodic basis (every hour). To avoid waiting after you apply the policy, you can run the Invoke-LapsPolicyProcessing PowerShell cmdlet (does require Administrator rights).
Windows LAPS Troubleshooting
Windows LAPS Event Logs
Windows LAPS logs can be found in the Windows Event Viewer at Applications and Services Logs > Microsoft > Windows > LAPS
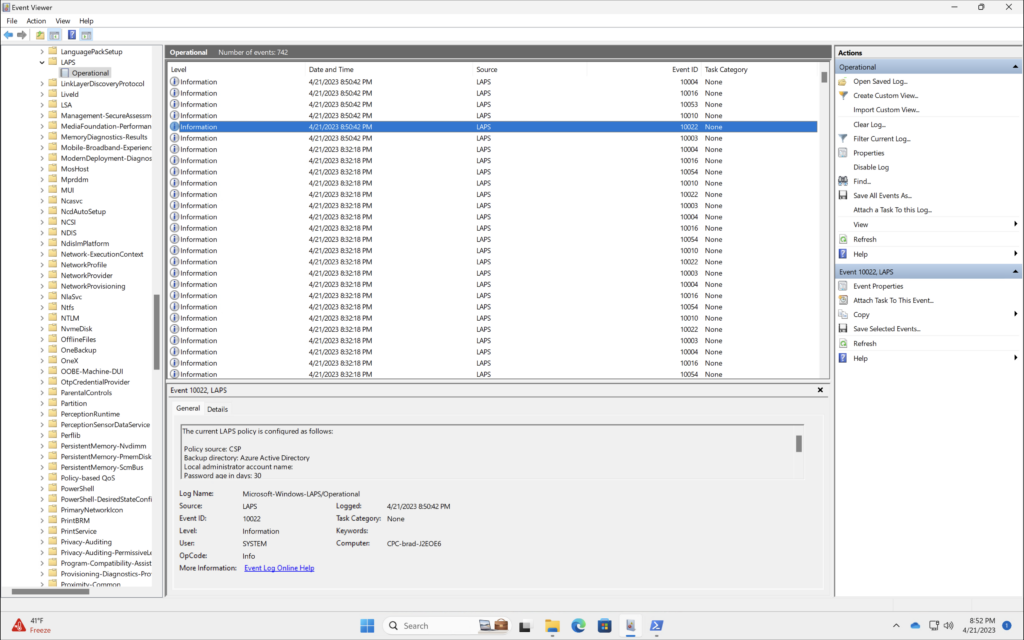
An overview of possible EventID’s relating to Windows LAPS can be found below:
| Event ID | Description |
| 10003 | LAPS policy processing is now starting. |
| 10004 | LAPS policy processing succeeded. |
| 10005 | LAPS policy processing failed with an error code. |
| 10021 | Policy is configured to back up the password to Windows Server Active Directory. |
| 10022 | Policy is configured to back up the password to Azure Active Directory. |
| 10023 | Windows LAPS is configured to use a legacy Microsoft LAPS policy. |
| 10018 | LAPS successfully updated Active Directory with the new password. |
| 10029 | LAPS successfully updated Azure Active Directory with the new password. |
| 10020 | LAPS successfully updated the local admin account with the new password. |
| 10031 | LAPS blocked an external request that tried to modify the password of the current managed account. |
| 10041 | LAPS detected a successful authentication for the currently managed account, and a background task has been scheduled for post-authentication actions. |
| 10042 | The post-authentication grace period expired per policy; configured post-authentication actions will now be executed. |
| 10043 | LAPS failed to reset the password for the currently managed account; the system will continue retrying the password reset operation. |
| 10044 | LAPS successfully reset the password for the currently managed account and completed all configured post-authentication actions. |
| 10033 | The machine is configured with legacy LAPS policy settings, but a legacy LAPS product is installed. The password will not be managed by Windows until the legacy product is uninstalled or newer LAPS policy settings are configured. |
| 10066 | LAPS received an LDAP_INSUFFICIENT_RIGHTS error trying to update the password using the LAPS password attribute. You should update the permissions on this computer’s container using the Set-LapsADComputerSelfPermission cmdlet |
| 10017 | LAPS failed to update Active Directory with the new password. The current password has not been modified. |
| 10015 | The managed account password needs to be updated due to one or more reasons (0x1A06) Account does not have a password expiration attribute The policy authority has changed The policy is configured for password encryption but the encrypted password attribute was not found The policy was changed to specify a different password encryption target Local state is missing and/or inconsistent with directory state |
| 10052 | LAPS is processing the current policy per normal background scheduling. |
| 10011 | LAPS failed when querying Active Directory for the current computer state. Error code: 0x80070031 |
| 10054 | LAPS is processing the current policy in response to a Group Policy change notification. |
| 10057 | LAPS was unable to bind over LDAP to the domain controller: |
PowerShell
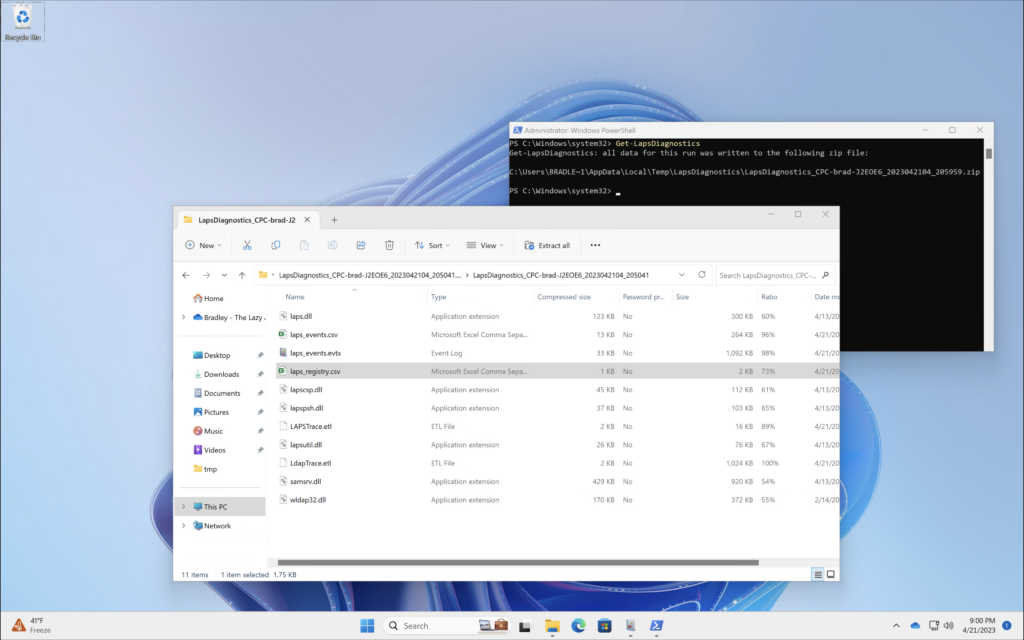
The Get-LapsDiagnostics PowerShell cmdlet collects Windows Local Administrator Password Solution (LAPS) logs and tracing from the local machine. Included in this zip is the current device configuration and an overview of the LAPS Windows Event Logs.
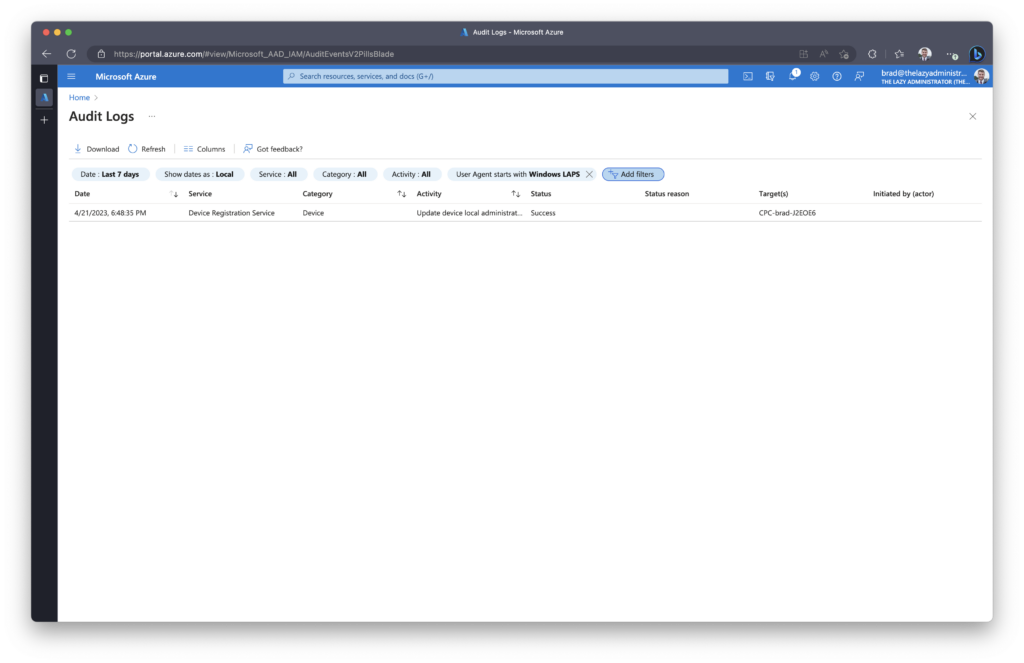
Azure Audit Logs
Windows LAPS events are also sent to Azure Audit Logs which can be viewed within the Azure Portal.

My name is Bradley Wyatt; I am a 5x Microsoft Most Valuable Professional (MVP) in Microsoft Azure and Microsoft 365. I have given talks at many different conferences, user groups, and companies throughout the United States, ranging from PowerShell to DevOps Security best practices, and I am the 2022 North American Outstanding Contribution to the Microsoft Community winner.
39 thoughts on “Windows LAPS Management, Configuration and Troubleshooting Using Microsoft Intune”
Hey Brad,
Thanks for sharing this informative step by step LAPs Integration.
I have a question, I can see all the features related to Windows LAPs in my Tenant
But cannot see this switch :
Azure Active Directory > Devices > Device Settings > Azure AD Local Administrator Password Solution (LAPS)
Do you have any idea?
Regards
Do you mean you cannot view the password for the device? Make sure the policy is applied to device and not a user. Also wait a few hours once you roll out the policy, it was not immediate for me
Please check the azure roles you have. I also had the same issue but when a person having more roles checked, he is able to see that
it Actually changed to Entra>Identity>Devices>All Devices>Device Settings> Azure AD Local Administrator Password Solution (LAPS)
This is a nice writeup, I have enjoyed articles from thelazyadmin for years.
Hi Brrad,
Thanks for you tuto.
It seems to me that it is still in pre-release but from your image, you have not (Windows insider Only).
Why is that?
It is in Public Preview, you should see it in your Intune Tenant
Wonderful piece of information
Great writeup, thank you.
On our aad joined windows devices, the local admin account is disabled by default. Just wondering if you know any good and secure solution for enabling them while using LAPS? Is it better to stay with the built-in or make a dedicated account?
I would re-enable them via policy or script prior to rolling our LAPS
Best to create a new local admin (I did so through a Powershell script) and assign it the LAPS config. The built in Administrator account has a well known SID and is easier to figure out for potential hackers..
This didn’t work.
Do we need to enable LAPS from Azure AD device settings?
Do we need to have local admin account already in place?
And yes, the policy is applied to device and not user.
While in public preview you may have to enable LAPS for your tenant. I just used the default local admin for Windows
You need to create the local admin user separately
https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/windows-laps-troubleshooting-guidance
I had error 10013 – which is – account not found
Hey Brad,
As shown above I have done all the settings but I cannot see LAPS password in intune portal nor in powershell, can you help me with it please. After completing policy I almost waited for a day but still I cannot see any password.
is it processing the policy, what do you see in logs
I got the password thanks, after searching for solution.
Hi Brad,
Thanks for that 🙂
I have an issue with the app registration and the redirect URI
I added the http://localhost.
Message: AADSTS50011: The redirect URI ‘https://login.microsoftonline.com/common/oauth2/nativeclient’ specified in the request does not match the redirect URIs configured for the application
Regards
I had this same error, I had to change the redirect URI to a mobile and desktop client URI instead of web.
If so, in that same pane, click to allow public flows
Also can be fixed by clicking the first checkbox in the URI’s
Thanks it works now 🙂
Have a good day
This was really helpful, especially the app registration steps. We are not currently managing devices in Intune. But our devices are HAADJ. I would like to take advantage of the Azure management option. This is possible with HAADJ devices not Intune managed, correct? As I understand it the Windows LAPS policy would be configured via GPO instead of Intune. Thanks!
I am not 100% but I believe it’s possible with HAADJ devices but I have no confirmed
Hi Brat, good article. Do we need to activate the local admin, or is that somewhere in the procedure? Default is disabled built-in local admin.
Hi Pieter, yes you have to activate the local administrator account (if using the built-in), the LAPS policy will not do that. If using Intune, create a settings catalog configuration policy for “Local Policies Security Options” and enable “Accounts Enable Administrator Account”.
If you try and push the admin activate policy before pushing the LAPS policy, it will most likely fail. The reason, the original password on the disabled administrator account doesn’t adhere to the current password policy requirement. Just wait until the LAPS policy has changed the password and the Intune policy has ben rerun, then it should be activated.
I want to create a custom role for our local IT guys to see the LAPS password but I don’t want to give them Intune admin access or Cloud device administrator access, is there a way we can create a custom role in Azure ad or any relevant solution?
My issue is that ‘User must change password at first logon’ setting is the default for the newly created admin account (via other means – custom OMA uri setting) and so even if LAPS has roatetd the pwd, I cannot login. 🙁
I, too, am running into this issue where the LAPS policy is configured and sometimes works; other times I get put in the LAPS password and the UAC prompt outputs “The user’s password must be changed before logging on the first time.”
Were you able to find a solution to this? I haven’t seen much related to this issue aside from your comment.
Thank You, this is perfect. I tried it in my lab environment and I was able to view the password in https://entra.microsoft.com/. However I do not see “Local admin password” option (which is between Recovery Keys and App configuration in one of your pictures above) when I go to Devices and i also do not see the rotate local admin password option in Intune. Any ideas?
My problem is one of our machines I had to reset due to compliance issues, it was assigned to user in auto pilot but they now have no admin rights and I can’t seem to deploy any rights to any of us admin guys, hoped setting up laps may solve solution but can’t figure how to get account setup on device, even if policy on intune setup. Without another reset how can this be resolved?
I did eventually get there – one thing I have come across is I set policy so new device autopiloted – pre-provisioned and on checking the admin account renamed, but of course it will not be able to backup LAPS password until actual user logged in for first time, this has left me in scenario of using the Shift F10 to see what’s happening and I notice the admin account renamed but on properties Password never expires is ticked, could this be standard ,has anyone noticed or is there a conflicting policy that won’t be able to apply until actual user logs in for first time.
Hey !
I Would like to extract windows LAPS on CSV file for all devices on my azure tenant !
Get-LapsAADPassword -DeviceIds
i have this but no idea how to do the rest ….
Great insights on Windows LAPS management! The step-by-step troubleshooting tips were particularly helpful. I appreciate how you broke down the configuration using Microsoft Intune. It made implementing the changes so much easier for me. Thanks for sharing!
Great insights on Windows LAPS management! The step-by-step approach to configuration using Microsoft Intune is especially helpful for those new to the process. Looking forward to more posts like this!
Great post! The step-by-step guide on configuring LAPS with Intune was incredibly helpful. I appreciate the troubleshooting tips too; they will definitely save time in the future. Looking forward to more insights!
Great post! I appreciate the step-by-step guidance on configuring LAPS with Intune. The troubleshooting tips are especially helpful—I’m sure they’ll save me a lot of time in the future. Thanks for sharing your insights!